
IP addresses are an essential part of today’s web infrastructure: Acting as virtual counterparts of real life addresses, they allow different electronic devices to communicate with each other. In certain cases, though, we may want to keep our IP address hidden or randomized: This is especially relevant for web scraping. Thankfully, there are multiple ways of achieving this — and in this article, we’ll explore several methods of generating a random IP address and hiding it.
What is an IP address?
As we’ve outlined in our recent overview of IP addresses, the definition goes: An IP (Internet Protocol) address is an alphanumeric address of a particular device on the web. As is the case with many technical definitions, this one holds a few interesting terms — let’s expand on them:
Internet Protocol. Although the web often looks like black magic, its principles of work are actually easy to understand: The web relies on various protocols which govern its different aspects like transmission of data, navigation, and more.
Alphanumeric: IP addresses are (usually) written with numbers. Here’s a typical example of an IP address, version 4: 182.16.255.1. There is also the version 6 of the internet protocol which utilizes both letters and numbers for their addresses: 2001:db8:0:1234:0:567:8:1 — IPv6 is designed to replace IPv4 because the latter protocol is unable to accommodate the ever-growing number of internet users.
Particular device. Each IP address is unique, meaning it’s assigned to a single device. Wi-Fi networks typically have multiple devices connected to them, so the “One device — one IP address” policy is crucial for helping us to differentiate between them.
On the web: There are multiple ways of data transfer between electronic devices (e.g. local area networks, Bluetooth networks), but IP addresses are only used on the internet. Still, the concept of addresses is present in these other methods, too: Bluetooth, for example, uses MAC addresses.
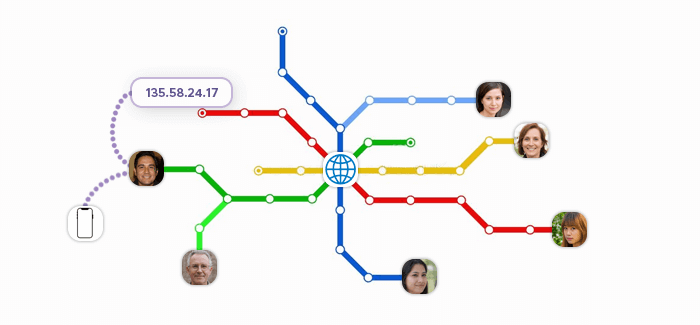
With this in mind, we can create a mental model of how IPs work: Upon connecting to the web, our device finds itself among millions of laptops, smartphones, tablets, smart home appliances, and so on. Having received a unique IP address, it can communicate with other devices and servers to transfer data across the web.
Why would you want to generate random IP addresses?
In most cases, your IP address is static, meaning it doesn’t change upon reconnecting to the internet. This is convenient for regular users — but when it comes to data collection, it presents a problem: Anti-web scraping systems use web scraping bots’ IP addresses to add them to block lists and prevent the bots from accessing the given website.
Regular users may want to generate random IPs, too: There are several uses for keeping your IP address changing:
Data Parsing
Data parsing and collection is crucial in a myriad of industries and use cases:
- It enhances business intelligence by providing reliable analytics.
- It captures detailed price data for price aggregators.
- It enables cybersecurity firms to perform cyber protection testing and research.
- It allows SEO professionals to work with their metrics with high precision.
Keeping the IP address unchanged hinders your data collection capacities, so you should try using random IPs instead.
Access Geo-Restricted Sites
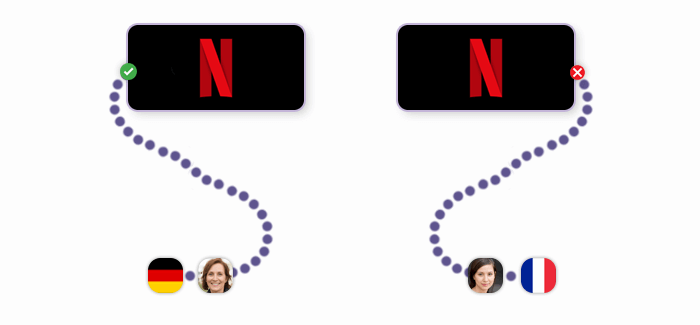
Bypassing restrictions is arguably the most common user scenario: Every day, dozens of web resources get blocked for different reasons (e.g. government restrictions or copyright infringement.) Government authorities typically block these websites in their country only, so changing the IP address (and, subsequently, its geolocation) solves this problem.
Browse Privately
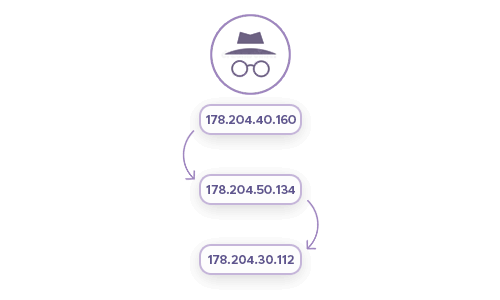
Anonymity is becoming relevant for more and more people: In an age of web tracking software, many users are wondering if they’re letting tech companies gather too much data about them. IP addresses are just that — addresses that can help to differentiate and track the given user, so making them random helps you preserve your privacy.
Security is the least obvious factor, but we shouldn’t underestimate it: Malicious third parties can use your IP address to attack you via DDoSing or injecting malicious code.
How to generate an IP address on your own?
There are several ways to do that — and it wouldn’t be correct to state that Tool A is always better than Tool B: Different people and different use cases call for different tools — let’s take a closer look at them and explore their pros.
VPN
VPN, a Virtual Private Network, is similar to proxies in how it works: Both these technologies act as a middleman between the user and the web server. VPNs are typically more user-friendly: They just need a client that only involves a few clicks to be up and running.
The downside of VPNs has to do with the difficulty to scale: It’s practically impossible to use them with numerous bots for data collection.
❔ Further reading: Comparing VPNs with Proxies and Exploring Their Use Cases
Dynamic IP address
In the section above, we mentioned that IP addresses can be static — but they can also be dynamic, i.e. change the address every time the user (re)connects to the internet. You can contact your internet service provider and request a dynamic IP address — most ISPs will give you one quickly and for free.
Like VPNs, this is far from a scalable solution: You’re still possessing only a single IP address and relying on the ISP to change it.
Tor Browser

Tor is a special web browser designed for web anonymity and security. It works via relays, connecting numerous users into the Tor network and helping them transfer the data of each other. Still, Tor’s pros — privacy and security — prove to be its cons, too: Its settings may be too complicated for the regular user. Relays, its security mechanisms, significantly decrease the user’s internet speed. Additionally, Tor doesn’t handle cookies too well.
Public Wi-Fi network

Public Wi-Fi networks serve countless users, so of course they assign random IPs to everyone. These networks, however, should be your last resort option: Transferring sensitive data over them is a security risk due to their nature — public and free, that is.
Risks of using free IP generators

A free random IP address generator seems like a great deal: You install an app/browser extension, click “I agree”, and start browsing the web. Here are a few reasons against using this kind of tools:
Poor Connection Speed
The most obvious downside that comes with free IP generators is performance: Your internet speed is likely to be much lower than usual. This is caused by large numbers of users on the network, who are all excited about acquiring a free random IP without paying anything – and this overloads the network.
Risk of Compromising Your Personal Information
A free random IP generator isn’t really free: Its developer simply chose a different monetization method: For example, upon installing this type of software, you may start seeing more ads. An even worse alternative is having your personal information sold to malicious third parties, which may try to use your data to commit identity fraud.
Dubious Source of IPs
Last but not least, the quality of free random IPs is subpar: Because of an unsustainable monetization model, their providers are unable to offer higher-quality IPs to their large user base. Thus, you’ll likely experience IP bans, CAPTCHAs, and other restrictions.
Best proxies to generate random IP addresses
A proxy is another great technology you can use to generate random IP addresses. Let’s take a closer look at several proxy types and see their differences:
Rotating proxies
As the name suggests, a rotating proxy server rotates your IP address: Built with peer-to-peer technologies, it provides great privacy and security — but it truly excels at data collection, ensuring that the anti-scraping systems don’t detect your web crawling bots.
The downside of rotating proxies may lie with the proxy provider: It’s crucial to work with ethical proxy providers — otherwise, you’re running the risk of using proxies that perform poorly and can easily be detected.
ISP Proxies
This proxy type combines elements from datacenter and residential proxies: It sources IP addresses from local internet service providers (ISPs), which come from datacenter servers rather than home devices like computers and smartphones.
Data Center Proxies
This type typically gets IPs from data centers and cloud hosting companies. Although it offers the most affordable prices, data center IPs have a higher chance of getting flagged due to the larger number of users.
Residential Proxies
This proxy type provides a dedicated IP from a specific country, city, and internet service provider. This allows you global access to any website for easy data collection and other tasks.
Why Choose Infatica’s Services?

Go global: Infatica’s proxies offer powerful geo-targeting capabilities, offering a set of major cities in the Americas, Europe, and Asia – you can now acquire real user IPs to create marketing strategies, perform search engine optimization, and more.
Easy-to-use – yet powerful: Infatica proxies can be managed via an easy-to-use web interface, which features traffic dashboards, quickstart guides, product & service overviews, and more. For power users requiring more fine-tuning capacities, Infatica offers a proxy management API for better scalability and refined control.
Less CAPTCHAs, more data: Infatica’s residential proxies help to avoid systems like reCAPTCHA and Cloudflare by routing traffic and masking the IP address, which has the added benefit of privacy. To the anti-bot systems, these requests now appear human-like – and your data collection pipeline will be much more successful. Even if a residential IP does get banned, Infatica’s proxy rotation feature ensures that it is quickly replaced with a new one.
Reliability you can count on: Infatica engineers work to keep our network as reliable as possible: We’ve managed to build a server infrastructure that boasts 99,9% uptime, low response time, and high request success rate – this allows our clients to get real user IPs without a hiccup.
Frequently Asked Questions
- 1. 10.0.0.0 - 10.255.255.255
- 2. 172.16.0.0 - 172.31.255.255
- 3. 192.168.0.0 - 192,168,255, 255
- 4 127.(any number).(any number)







