An SSL proxy is a powerful tool for data collection bots and anonymity. If you want to utilize it to its full potential, use this guide to learn about how an SSL proxy works, its use cases, scalability, IP rotation, strengths, and weaknesses.
How does SSL proxy work?
An SSL proxy works by acting as an intermediary between a client (such as a web browser) and a server (such as a web server). When a client requests a secure connection to a server, the SSL layer intercepts this request and establishes a secure SSL/TLS connection with the client. Simultaneously, the proxy sets up a separate SSL/TLS connection with the server.
This dual connection allows the proxy to decrypt and inspect the data flowing between the client and the server before re-encrypting it and forwarding it to the intended destination. The SSL proxying process ensures that data remains secure and private throughout its journey, while also allowing the proxy to filter or modify the data if necessary.

Types of SSL proxies
Let’s take a closer look at various secure sockets layer (SSL) subtypes:
Forward SSL proxies
The forward subtype is essentially the standard SSL one. It’s commonly used in several scenarios:
- Security and Monitoring: In corporate environments, it’s used to enforce security policies. By decrypting and inspecting SSL traffic, organizations can detect and block malicious content, prevent data leaks, and ensure compliance with regulatory requirements. This is particularly important for monitoring SSL-encrypted traffic that would otherwise bypass traditional security measures.
- Content Filtering: Schools, libraries, and businesses often use forward proxies to filter web content. By decrypting traffic, the proxy can block access to inappropriate or non-compliant websites, ensuring that users adhere to acceptable use policies.
- Performance Optimization: Forward proxies can cache frequently accessed content and perform data compression. This reduces bandwidth usage and speeds up access to commonly used resources, improving overall network performance.
- Anonymity and Privacy: Individuals concerned about privacy can use forward proxies to hide their IP addresses and encrypt their internet traffic, making it more difficult for websites to track their online activities.
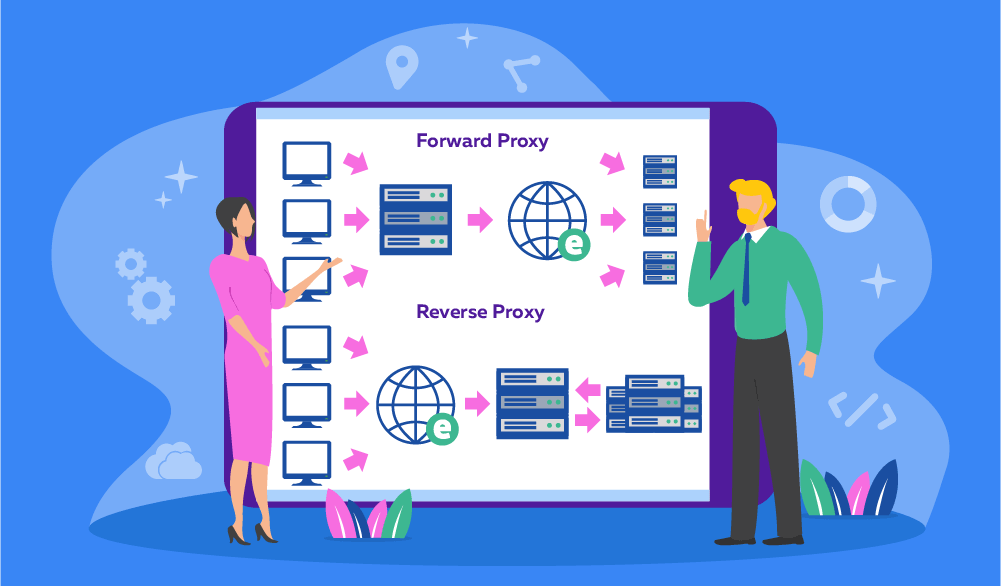
Reverse SSL proxies: Functions and use cases

On the other hand, a reverse proxy’s workflow, as the name suggests, is reversed: It sits between external clients and a web server, intercepting incoming requests before they reach the server. When a client initiates a secure connection to a server, the reverse proxy handles this request, establishing an SSL/TLS connection with the client. It then decrypts the incoming data, processes it, and either forwards it to the appropriate internal server over an internal network or re-encrypts it and forwards it if necessary.
Reverse proxies are commonly used in several scenarios:
- Load Balancing: They can distribute incoming traffic across multiple backend servers to balance the load, ensuring no single server becomes overwhelmed. This improves the availability and reliability of web services by preventing server overload and downtime.
- SSL Offloading: By handling TLS/SSL encryption and decryption tasks, reverse proxies offload this computationally intensive work from backend servers. This frees up server resources, allowing them to focus on delivering content and handling application logic, resulting in improved performance.
- Security Enhancement: They can also enhance security by terminating the SSL connection and inspecting incoming traffic for malicious content or attacks before they reach the backend servers. This allows organizations to apply security policies, detect and block threats, and protect sensitive data.
- Web Acceleration and Caching: Reverse proxies can cache static content and frequently requested resources. By serving cached content directly to clients, they reduce the load on backend servers and speed up response times, providing a better user experience.
- Application Firewall: Last but not least, they can act as a web application firewall, protecting backend servers from various web-based attacks such as SQL injection, cross-site scripting (XSS), and other exploits by filtering and blocking malicious requests.
Transparent SSL proxies: Overview and applications
Transparent proxies differ from the other types primarily in their mode of operation and how they interact with clients and servers. A transparent proxy intercepts and processes SSL traffic without requiring any configuration changes on the client side. Clients are unaware of the proxy's presence because their requests are automatically redirected and handled by the proxy without any explicit proxy settings in their applications or devices.
Companies typically use them in these scenarios:
- Network security: Transparent proxies are often used in organizational networks to enforce security policies. By inspecting encrypted traffic, they can detect and block malicious content, unauthorized data transfers, and other security threats without requiring users to configure proxy settings, increasing network security.
- Content filtering: Educational institutions, businesses, and public networks use transparent proxies to filter web content and enforce acceptable use policies. This ensures compliance with regulations and internal policies by controlling access to specific websites or types of content.
- Monitoring and compliance: Transparent proxies enable organizations to monitor and log web traffic for compliance purposes. This is especially important in regulated industries where it is necessary to track and audit access to sensitive information.
- Performance management: By caching frequently accessed content and optimizing network traffic, transparent proxies can enhance overall network performance. This reduces latency and bandwidth usage, providing a smoother user experience.

Distinction between dedicated and shared SSL proxies
| Dedicated | Shared | |
|---|---|---|
| Operation |
Assigned to a single user or organization. This means that the resources and IP addresses associated with the proxy are used exclusively by one client.
No other users sharing the bandwidth or computational resources, often resulting in faster and more reliable performance.
Users have more control over the proxy settings and can tailor the proxy’s configuration to meet their specific needs without worrying about conflicts with other users.
|
Used by multiple users or organizations simultaneously. The resources and IP addresses associated with the proxy are distributed among several clients.
Generally more affordable because the cost of the infrastructure is spread across multiple users.
Performance can vary depending on the number of users and the amount of traffic at any given time. Peak usage times may result in slower speeds and reduced reliability.
|
| Use cases |
Ideal for organizations that handle sensitive data, such as financial institutions or healthcare providers, where data security and privacy are paramount.
Suitable for businesses that generate a significant amount of traffic and require consistent, high-speed access without the risk of bandwidth throttling or performance degradation.
Beneficial for users who need customized proxy configurations, such as specific routing rules or security settings tailored to their operations.
|
Ideal for individuals or small businesses with limited budgets that require basic proxy functionalities without the need for exclusive resources.
Suitable for users who need proxy services for general web browsing, occasional secure transactions, or bypassing geo-restrictions without high performance or security demands.
Useful for applications where consistent performance is not crucial, such as testing or occasional use scenarios
|
What benefits does an SSL proxy server offer?
You would typically use this proxy type for these benefits:
Enhancing your online privacy and security

These proxies significantly enhance online privacy and internet security by encrypting the data transmitted between your device and the internet. This encryption technology ensures that any information you send or receive is protected from eavesdropping, interception, and tampering by malicious actors. By using proxies, your online activities are hidden from third parties, including internet service providers (ISPs) and potential hackers, making it much harder for them to access sensitive information such as login credentials, financial data, and personal communications.
Additionally, proxies can help mask your IP address, adding an extra layer of anonymity. This prevents websites from tracking your browsing habits and building detailed profiles based on your internet usage. By anonymizing your IP address, proxies also protect you from targeted cyberattacks and reduce the risk of being a victim of intellectual property theft or online fraud.
Accessing geo-restricted websites or content
You can also bypass geo-restrictions and access content that may be unavailable in their region. By routing your internet traffic through a target server located in a different geographic location, proxies make it appear as though you are accessing the internet from that location. This is particularly useful for accessing streaming services, websites, or online services that are restricted to certain countries or regions due to licensing agreements or government censorship.
For example, if a streaming service offers different content libraries based on the user's location, a proxy can help you access a broader range of movies and TV shows by connecting through a server in a region with more extensive offerings. Similarly, if you are traveling abroad and wish to access services or websites that are only available in your home country, it can help maintain access to those resources.
SSL proxy server use cases
The SSL subtype is used in various scenarios – here are the most popular ones:
Providing extra anonymity
These proxies provide an additional layer of anonymity by masking the user's IP address and using end-to-end encryption for their internet traffic. This makes it difficult for websites, advertisers, and third parties to track online activities or identify the user's real location. Enhanced anonymity is particularly valuable for individuals concerned about privacy, journalists working in restrictive environments, and anyone concerned about data leaks.
Safer web data scraping
Using proxies for web scraping offers more access and enhances safety and efficiency by providing anonymity and reducing the risk of visiting blocked websites. Rotating SSL proxies can use multiple IP addresses, distributing scraping requests to avoid detection and bypass blocks.
Managing social media accounts
Proxies are essential for managing multiple social media accounts, especially when handling accounts for clients or running large-scale marketing campaigns. By using different IP addresses through proxies, social media managers can avoid suspension and bans that often result from logging into multiple accounts from a single IP.
Shopping for exclusive items
For shopping exclusive or limited-edition items, proxies help bypass geographic restrictions and local availability limitations. By connecting through a proxy server in a different region, users can access product releases and sales that are not available in their home country. This enables shoppers to purchase high-demand items such as concert tickets, limited-edition merchandise, or region-exclusive products without facing geo-blocks.
Ad verification
Proxies play a crucial role in ad verification by allowing advertisers to view and verify their ads from different locations. This ensures that the ads are displayed correctly and are reaching the intended audience. By simulating different geographic locations, advertisers can monitor ad placement, check for ad fraud, improve performance of their ad campaigns, and confirm that their ads comply with regional regulations and standards.
Brand protection

Proxies help monitor the internet for counterfeit products, trademark infringements, and unauthorized use of brand assets. By scanning websites from various IP addresses and locations, companies can detect and take action against online threats to their brand. Proxies enable continuous, comprehensive monitoring without revealing the organization's IP address.
Preventative cybersecurity
Proxies can provide an additional layer of defense against cyber threats. By encrypting data and masking IP addresses, they protect the company’s mission-critical assets against interception, hacking, and other malicious activities. They are especially useful in preventing targeted attacks, performing network segmentation, securing communications, and ensuring that sensitive information remains confidential. In some scenarios, they can even emulate threats to test the company’s infrastructure.
Are SSL and HTTPS proxies similar?
SSL and HTTPS proxies are similar in that they both provide encrypted communication channels, enhancing security and privacy. However, there are some key differences in their functions and implementations.
When it comes to encryption, both SSL and HTTPS proxies use SSL/TLS protocols to encrypt data between clients and the proxy servers, ensuring that the data transmitted is secure and protected from eavesdropping and interception. Also, they both improve privacy, masking the user's IP address, providing an additional layer of anonymity and preventing websites from tracking the user's real location.
Their differences lie in functionality: HTTPS proxies are designed specifically to handle HTTPS traffic, meaning they only work with web traffic that uses the HTTPS protocol. These proxies decrypt and re-encrypt data online from HTTPS connections, allowing them to inspect, filter, or modify the content if necessary. The SSL type, on the other hand, can handle any type of traffic that uses SSL/TLS encryption, not just HTTPS. This includes other protocols like FTPS (FTP Secure), SMTPS (SMTP Secure), and IMAPS (IMAP Secure).
They also have different use cases: HTTPS proxies are typically used for web browsing, accessing secure websites, and filtering web content. They are particularly useful in corporate environments for enforcing internal internet usage policies and securing web traffic. The SSL type is more versatile and can be used for a variety of secure communication needs, including securing email communications, file transfers, and other applications that use SSL/TLS.
SSL proxy server challenges and considerations
We’ve taken a closer look at their strengths and benefits – but what are their downsides? Performance overhead can be a factor: SSL/TLS encryption adds computational overhead to secure transmission of data, which can result in slower connection speeds and increased latency, especially on devices with limited processing power or high traffic volumes. This can impact user experience, particularly for latency-sensitive applications like online gaming or real-time communication.
Compatibility issues: SSL/TLS protocols evolve over time, and older versions may have compatibility issues with newer security standards or encryption algorithms. This can lead to compatibility issues between clients and servers, resulting in connection failures or degraded security if outdated protocols are used.
Configuration: Setting SSL/TLS up correctly requires careful attention to encryption settings, SSL certificate management, and server configurations. Misconfigurations or errors in SSL/TLS settings can weaken security, expose vulnerabilities, or cause compatibility issues. Additionally, managing SSL server certificates, including renewal, revocation, and key management, can be complex and time-consuming, especially in large-scale deployments.
Security vulnerabilities: While SSL/TLS protocols are designed to provide secure communication, they are not immune to security vulnerabilities or attacks. Over the years, various vulnerabilities, such as POODLE, Heartbleed, and BEAST, have been discovered in SSL/TLS implementations, requiring patches and updates to mitigate potential risks. Additionally, SSL interception techniques used by some security products can introduce security vulnerabilities if not implemented correctly.
What are the alternatives to an SSL proxy server?
Several alternatives exist, each offering unique features and use cases. Here are some tools and utilities – and reasons you might choose them over proxies:
Virtual Private Network (VPN)
VPNs encrypt all internet traffic from your device, not just web traffic, providing comprehensive privacy and security. They also offer features like IP masking, server selection, and protocol options, making them suitable for various online activities beyond web browsing.
VPNs are ideal for users who prioritize privacy and security across all internet activities, including web browsing, file sharing, online gaming, and streaming media. They are also useful for bypassing geo-restrictions and accessing region-locked content.
Tor Network
The Tor network anonymizes internet traffic by routing it through a series of volunteer-operated nodes, concealing the user's IP address and location. It offers a high degree of anonymity and is resistant to traffic analysis and surveillance.
Tor is suitable for users seeking maximum anonymity and privacy, particularly in regions with internet censorship or surveillance. It's commonly used by activists, journalists, whistleblowers, and individuals in repressive regimes.
SSH Tunnels
SSH (Secure Shell) tunnels encrypt and route internet traffic through an SSH server, providing secure communication between the client and server. They offer a lightweight and flexible solution for secure data transmission and remote access.
SSH tunnels are beneficial for secure remote access to servers, accessing internal resources from external networks, and bypassing network restrictions in restricted environments like corporate networks or public Wi-Fi hotspots.