- What is an antidetect browser?
- How to check its effectiveness
- Octo Browser: Multi-profile browsing
- MoreLogin: Enhanced login management
- AdsPower: Ad-blocking capabilities
- Dolphin Anty: Antivirus and security features
- Kameleo: Advanced browser fingerprinting protection
- GoLogin: Multi-account management
- MuLogin: Anonymous browsing with multiple profiles
- Incogniton: Focus on privacy and incognito mode
- Multilogin: Seamless management of multiple profiles
- Lalicat: Customizable and privacy-focused
- VMLogin: Virtual machine-based browsing for security
- Ghost Browser: Session management and workspace organization
- Importance of proxies for antidetect browsers
- Risks and challenges in web scraping
- How do antidetect browsers help with web scraping?
- What are other use cases for antidetect browsers?
- Frequently Asked Questions


Antidetect browsers have helped web scraping to grow in popularity among people who need to collect data for analysis purposes, as they’re effective and time-saving. However, this is becoming more challenging as more websites implement more sophisticated anti-bot and user profiling techniques. Web scrapers can benefit from an increase in privacy provided by antidetect browsers by keeping their data anonymous and avoiding being blocked. This article will cover exactly this topic. We will discuss challenges in web scraping and how these 12 best antidetect browsers can deal with them.
What is an antidetect browser?
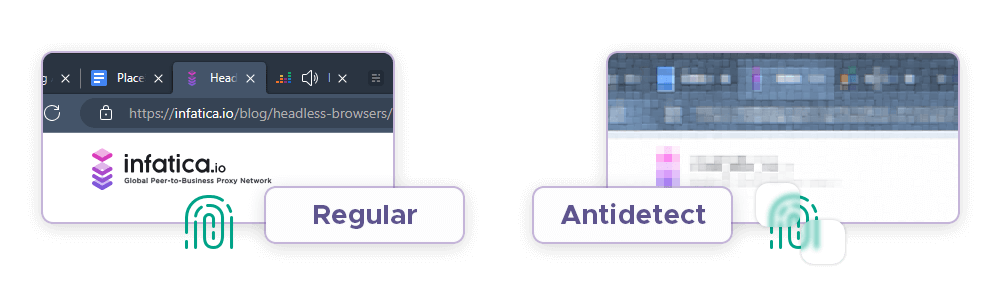
An antidetect browser works by creating and managing multiple virtual browser profiles that have different settings and digital fingerprints. Each profile can emulate a different operating system, browsing environment, version, user agent, IP address, and other identifying information that websites use to track visitors. The profiles are also updated and synchronized with real device fingerprints to avoid detection.
Anti-detect browsers also use proxy servers, encrypted tunnels, and other techniques to reroute and secure the data transmissions between the user and the website. This way, the website cannot see the user’s real location, identity, or activity. This technology also allows the user to disable or spoof cookies, browser plug-ins, and other tracking methods that websites use to collect personal information.
How to check its effectiveness
To check the effectiveness of anti-detect browsers, you can use some online tools that verify your digital fingerprint data. These tools can show you how and what data is viewed by various websites and their security systems. Some examples of these tools are Pixelscan, IPhey, Whoer, and Browserleaks.
By using these tools, you can compare the data that your browser shows to the websites with the data that your real device has. You can also check if it can spoof or change the data that websites use to identify and track visitors, such as cookies, unique IP addresses, user agents, and browser fingerprints. The more browser data you can spoof or change, the more effective your software is.
1. Octo Browser: Multi-profile browsing

Octo Browser is a multi-accounting browser that allows you to create and manage any number of accounts on various services without hassle, IP bans and extra expenses. Like Google Chrome, It is based on Chromium and supports proxy, cookie, fingerprint and automation features. It also offers quick and easy access to your profiles with no setup or configuration required. Some of the key features of Octo Browser are:
- Teamwork: Transfer or share browser profiles with team members while keeping fingerprints intact. Use it for managing multiple accounts on different devices with no checkpoints and bans for multi-accounting.
- Automation: Automate all account and profile interactions via an API using Puppeteer, Selenium or any other libraries. Import cookies in json and Netscape formats and automate cookie collection with the built-in cookie robot in parallel headless mode.
- Quality fingerprints: Control all fingerprint parameters and spoof or change the data that websites use to identify and track visitors. The unique digital fingerprint is managed in the Chromium code, which protects your device against additional checks. Each profile has a distinct browser fingerprint of a real machine that is updated and synchronized with real device fingerprints to avoid detection.
- Support: Octo Browser provides technical support via a Telegram bot and a detailed video tutorial to help you get started and use the browser effectively.
- Security: Octo Browser uses proxy servers, encrypted tunnels, and other techniques to reroute and secure the data transmissions between you and the website. It also allows you to disable or spoof cookies, browser plug-ins, and other tracking methods that websites use to collect personal information.
2. MoreLogin: Enhanced login management

MoreLogin is anti-detect software that enables you to create and manage multiple browser profiles from one device. Each profile has a unique fingerprint that masks your behavior, helping you avoid detection and bans while surfing online. Some of the key features of MoreLogin are:
- 24/7 support: Get product support and customer service via a Telegram bot, as well as access the latest industry news and product features.
- Account management: Securely log in to your accounts within each browser profile, which acts as a new physical device.
- Teamwork: Transfer or share browser profiles with your team members while keeping fingerprints intact.
- Proxy integration: Use proxy servers, encrypted tunnels, and other techniques to reroute and secure the data transmissions between you and the website. Integrate with popular proxy providers such as Infatica.

3. AdsPower: Ad-blocking capabilities

AdsPower is a solid Multilogin alternative that enables you to create and manage multiple accounts with different browser fingerprints, proxies and websites. It has positive reviews from customers who use it for various purposes, such as managing e-commerce business, marketing and personal use. Some of the key features of AdsPower are:
- Fingerprint control: You can control and customize all fingerprint parameters, such as operating systems, browser, user agent, different proxy IPs, and more.
- Flexible pricing: You can choose from different pricing plans based on your needs and budget.
- Account importing: You can securely import your existing accounts from other browsers or platforms and use them in AdsPower with no hassle. Export your accounts and cookies in various formats.
- Profile sync: You can sync your browser profiles across different devices and access them anytime, anywhere. Transfer or share your profiles with your team members while keeping fingerprints intact.

4. Dolphin Anty: Antivirus and security features

Dolphin Anty browser is optimized to perform multiple account creation for affiliate marketing and social media accounts. It is based on Chromium and supports proxy, cookie, fingerprint and automation features. It also offers quick and team management and easy access to your profiles with no setup or configuration required. Some of the key features of Dolphin Anty are:
- Account status tracking: Monitor the activity and performance of your accounts in real time. View detailed statistics and reports on your campaigns and conversions.
- Bulk actions: Perform multiple actions on your accounts simultaneously, such as logging in, posting, liking, commenting, and more. Automate these actions with scripts and schedules.
- Proxy manager: Integrate with popular proxy service providers such as Infatica and perform bulk management of proxies.
5. Kameleo: Advanced browser fingerprinting protection

Kameleo allows you to create and manage multiple custom browsers with mobile support and fingerprints. It offers quick and easy access to your profiles with no setup or configuration required. Some of the key features of Kameleo are:
- Profile management: Create, save, load, and share unlimited browser profiles to spoof fingerprints. Import and export cookies in various formats and automate cookie collection with a built-in robot.
- Web browser automation: You can start hundreds of virtual browser profiles with a few lines of code using Kameleo Local API. Manage them with your favorite automation frameworks, such as Selenium, Puppeteer, or Playwright.
6. GoLogin: Multi-account management

GoLogin enables users to run multiple separate browsing profiles for real device imitation to conceal your identities. It is based on Chromium and supports proxy, cookie, and Tor integration. It also offers an intuitive interface and quick and easy access to your profiles with no setup or configuration required. Some of the key features of GoLogin are:
- Fingerprint customization: Control and customize over 50 fingerprint parameters, such as operating system, browser, user agent, IP address, and more. Use real canvas fingerprints collected from billions of users worldwide to pass website detections.
- Profile management: Create, save, load, and share unlimited browser profiles with different fingerprints. Import and export cookies in various formats and automate cookie collection with a built-in robot.
- Web browser automation: Start hundreds of unconnected profiles with a few lines of code using GoLogin Local API access. Manage them with your favorite automation frameworks, such as Selenium, Puppeteer, or Playwright.
7. MuLogin: Anonymous browsing with multiple profiles

MuLogin can be used to create and manage multiple accounts on various platforms without detection. It also quick and easy access to your profiles with no setup or configuration required. Some of the key features of MuLogin are:
- Independent fingerprint profiles: Create unique fingerprints during batch profile creation. Each browser’s fingerprint environment, cookies, local storage, and other cache files will be completely isolated, and the browser profiles cannot leak information to each other, so as to achieve multi-account secure login without being detected.
- Web browser automation: Automate all account and profile interactions via the REST API using Puppeteer, Selenium or any other libraries. Import cookies in json and Netscape formats and automate cookie collection with the builtin cookie robot in parallel headless mode.
- Teamwork: Transfer or share browser profiles with team members while keeping fingerprints intact.

8. Incogniton: Focus on privacy and incognito mode

Incognition can run multiple separate browsing profiles to conceal your identities. Some of the key features of Incognition are:
- Full data control: You can control and customize all the data that websites use to identify and track visitors, such as cookies, IP addresses, user agents, and browser fingerprints. Disable or spoof browser plug-ins, webRTC, and other tracking methods that websites use to collect personal information via bulk actions.
- Multiple profiles management: You can create, save, load, and share unlimited browser profiles with different fingerprints.
- Web browser automation: You can start hundreds of virtual browser profiles with a few lines of code using Incognition Local API. You can also manage them via Selenium integration.

9. Multilogin: Seamless management of multiple profiles

Multilogin browser lets you perform web automation tasks and manage multiple browser profiles with different settings and fingerprints. Some of the key features of Multilogin are:
- Modifying browser fingerprints: Control and customize over 50 fingerprint parameters, such as operating system, browser, user agent, IP address, and more. Use real canvas fingerprints collected from billions of users worldwide to pass website detections.
- Integration tools: Integrate Multilogin with popular automation frameworks and cross-device sync, such as Selenium, Puppeteer, or Playwright, using its open API. Use its browser extensions to manage multiple API calls and browser profiles.
- Customized browsers: Choose from different browser engines, such as Mimic, Stealthfox, or Chrome, to create custom browsers that suit your needs and preferences.
- Military-grade encryption: Protect your browser profiles and store them locally or in the cloud.
10. Lalicat: Customizable and privacy-focused

Lalicat enables you to create and manage multiple browser profiles with different settings and fingerprints. Some of the key features of Lalicat are:
- Multi-language support: Use Lalicat in different languages, such as English, Chinese, Russian, Spanish, and more. You can also change the language of the browser interface and the websites you visit.
- Tor network: Utilize the Tor network to browse the web anonymously and securely. You can also switch between Tor and regular proxies with one click.
- Easy startup: Start Lalicat with a simple double-click on the desktop icon. Use the command line or the API to launch Lalicat with custom parameters.

11. VMLogin: Virtual machine-based browsing for security

VMLogin offers quick and easy automation of your profiles. Some of the key features of VMLogin are:
- Creating separate browsing environments and virtual sessions: Each browser’s fingerprint environment, cookies, local storage, and other cache files are completely isolated and cannot leak between profiles. This way, you can achieve multi-account secure login without being detected.
- Easy team collaboration: Transfer or share browser profiles with your team members while keeping fingerprints intact.
- Built-in and third-party automation features: Automate all account and profile interactions via an API using Puppeteer, Selenium or any other libraries. You can also import cookies in json and Netscape formats and automate cookie collection with the builtin cookie robot in parallel headless mode. Last but not least, use third-party visual automation constructors like Browser Automation Studio to manage multiple API calls and browser profiles.
12. Ghost Browser: Session management and workspace organization

Ghost Browser enables you to run multiple separate browsing profiles with immediate setup to conceal your multiple identities. Some of the key features of Ghost Browser are:
- Session management: Create multiple sessions within one browser window, each with a different color-coded tab. Each session has its own cookie jar and fingerprint, allowing users to log into numerous accounts on the same website without detection.
- Workspace organization: Organize your sessions into different workspaces, such as personal, work, or project-based. Save, restore, and share your workspaces with your team members or clients.
- Web browser automation: Automate your browsing tasks using Ghost Browser’s extension tools, such as Ghost Proxy Control, Ghost Inspector, and Ghost Click.
Importance of Proxies for antidetect browsers
By using proxies with anti-detect software, users can achieve a higher level of online privacy and security. They can use IP masking to conceal identifying information from websites they visit, protecting their online identity and anonymity. They can also access geo-restricted content or bypass internet censorship, which may not be possible with regular browsers.
Proxies are essential for these browsers because they provide the first layer of protection against website detection and tracking. They provide the second layer of protection by modifying other data that websites use to identify and track visitors. Together, a proxy service and anti-detect software can help users with various online tasks and protect their privacy and security.
However, certain proxy risks can arise if you’re using free proxies from unreliable providers: These risks can include malware, worse device performance, and more. To avoid these problems, we advise you to use residential proxies from reputable companies.
Risks and challenges in web scraping
Web scraping can be a powerful tool for data collection, but it also comes with risks and challenges that need to be considered. Some of the main issues with web scraping include:
Anti-Scraping Systems

These systems are designed to prevent bots and other automated tools from accessing site content and can make it difficult to collect data. Some sites use CAPTCHAs or other tools to verify that users are humans, while others may block IP addresses or user agents that are associated with scraping activity.
Getting Blocked
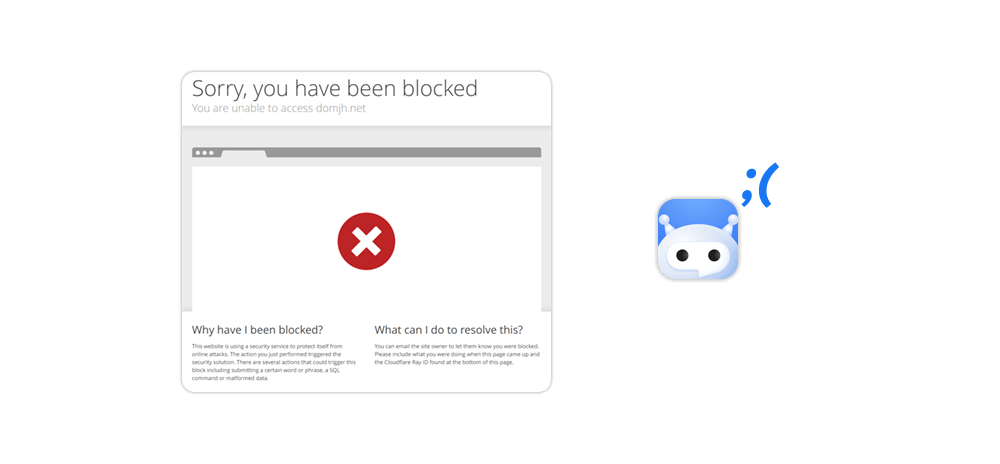
Even if a site does not have anti-scraping measures in place, web scrapers can still be blocked if they send too many requests in a short period of time. This can be particularly problematic for large-scale scraping projects that involve collecting data from multiple sites. To mitigate this risk, it is important to use proxies and rotate user agents, among other techniques.
Dynamic Content
Dynamic content refers to content that changes based on user input or other factors, such as the time of day or location. This can make it difficult to collect accurate data since the scraper may not know what content to look for or where to find it. To overcome this challenge, it is important to carefully consider the structure of the site being scraped and to use tools such as regular expressions to identify and extract specific data.
How do antidetect browsers help with web scraping?
Best antidetect browsers provide web scrapers with an additional layer of privacy and security. They enable internet users to access the internet anonymously and avoid being tracked or blocked by websites that might be able to do so. As a result, the risks associated with web scraping are significantly reduced.
Here are some of the benefits of using anti-detect browsers like AdsPower.
Spoof browser fingerprints
A browser fingerprint is a combination of information collected by websites every time you visit them. These pieces of information could include device model, browser version, language and keyboard settings, user agent, and a lot more. AdsPower can modify your browser fingerprints to make it appear that another user is accessing the website. If you use AdsPower together with proxies, you will also be able to mask your real location.

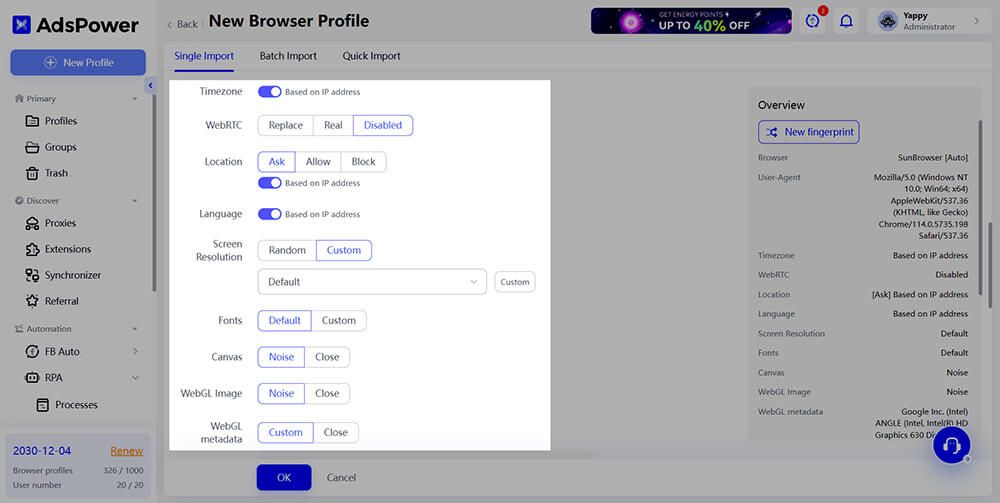
Protect online privacy
Maintaining online anonymity is simple with AdsPower's privacy-focused browser features, such as data spoofing, Canvas and WebGL disabling, and proxy integration. For example, you can use the direct proxy integrations of the browser to perform IP rotation, which involves changing the web scraper's IP address to evade detection by websites that might be blocking or keeping an eye on their activity.
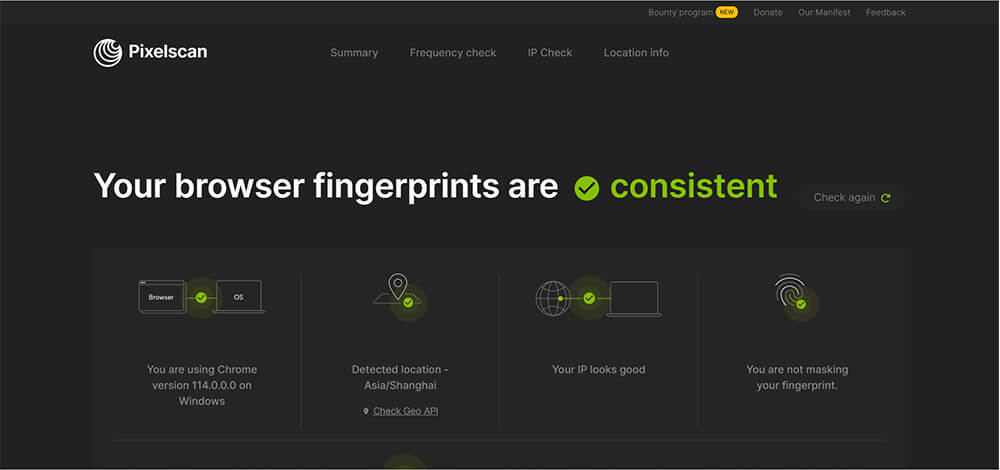
Bypass anti-bot systems
There are various techniques that can be used to bypass anti-scraping measures, including rotating user agents, implementing delays between requests, and using proxies. Captchas and IP blocking can be circumvented with these methods. With an anti-detect browser, you can effectively manage these measures.
Automate scraping tasks
Browser automation can improve effectiveness and cut down on the amount of time needed for web scraping. An anti-detect browser is always equipped with built-in automation features. For example, AdsPower has an RPA robot feature that allows you to design and execute automation tasks on any platform.
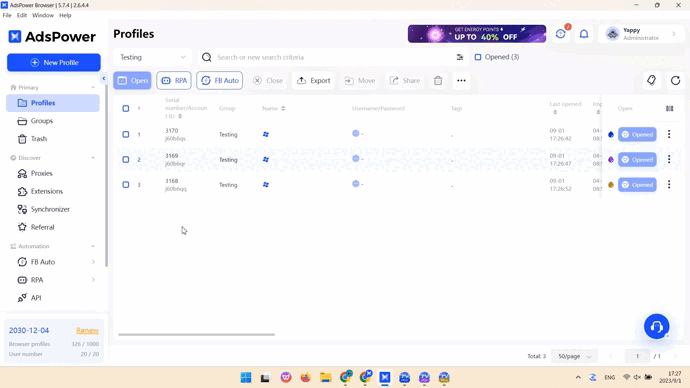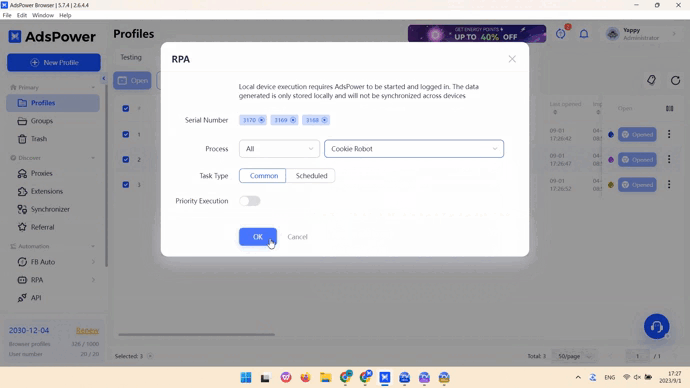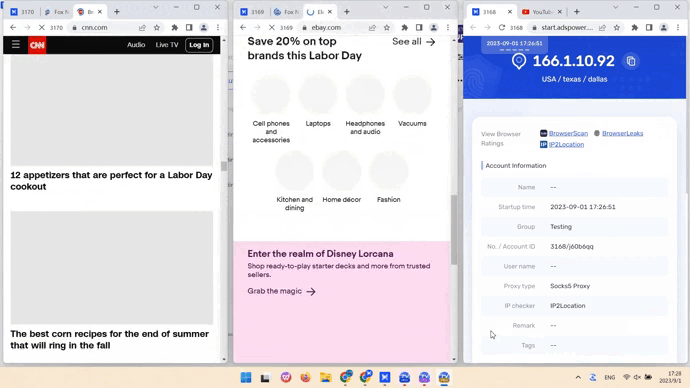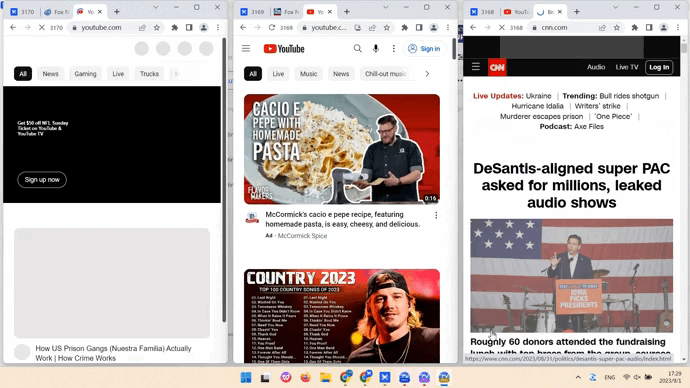
Scale data collection with multiple browser profiles
In AdsPower, you can create unlimited virtual profiles that don’t overlap with each other. These profiles are configured with generated fingerprints, so each of them appears to be a separate device. When running web scrapers in the profiles, you will be able to collect data from different sources simultaneously, accessing geo-restricted websites and avoiding detections.
What are other use cases for antidetect browsers?
Their biggest strength is anonymity. So, in principle, they can be used by all privacy-concerned crowds, including online marketers, e-commerce vendors, IT experts, etc. Yet there are industries that rely on anonymization browsers more than others. Here are some of the most common use cases for an anti-detect browser.
Affiliate marketing
Affiliate marketers or marketing agencies usually have to manage multiple social media accounts or ad accounts for the purpose of promoting offers. When they run these accounts from one device or one IP address, this often ends up leading to the accounts being banned, which turns out to be the biggest challenge for them. In this situation, anti-detect browsers are an effective solution for marketers and agencies thanks to their ability to create more than one identity.
Crypto whitelisting and airdrops
To expand the possibility of getting access to a crypto whitelist or an airdrop, a relatively easy method is to manage accounts to submit whitelist applications or complete designated tasks for social media managers. And yet again, to bypass blocks and bans, the best antidetect browsers come into play.
E-commerce
Many sellers believe that the key to succeeding in e-commerce is to expand their revenue streams by setting up multiple online storefronts, but the problem is account bans from platforms. An anonymization browser, in this case, gives vendors access to unlimited profiles that are perceived as real merchants.
Conclusion
Browser fingerprinting can make web scraping extremely hard. You must cover a lot of ground if you want to remain undetected. Anti-detect technologies like AdsPower are a great way to maintain anonymity and enhance the effectiveness of data collection. They can also help you scale your business in other industries.








