Both proxies and firewalls are invaluable network tools — and with their rich functionality, it's tempting to think that they're interchangeable. Let's explore them in greater detail: How do they work? What are their use cases? Is one better than the other?
What Is a Firewall?
A firewall is a network security system designed to monitor and control incoming and outgoing network traffic based on predetermined security rules. It serves as a barrier or filter between trusted internal networks and untrusted external networks, such as the internet, to protect systems from unauthorized access, cyberattacks, and other security breaches.
Firewalls can be implemented through hardware, software, or a combination of both – and their primary function is to examine packets of data sent across the network and either allow or block them based on the security policies set by the administrator. This is crucial in maintaining the integrity, confidentiality, and availability of information within a network.
How a Firewall Works
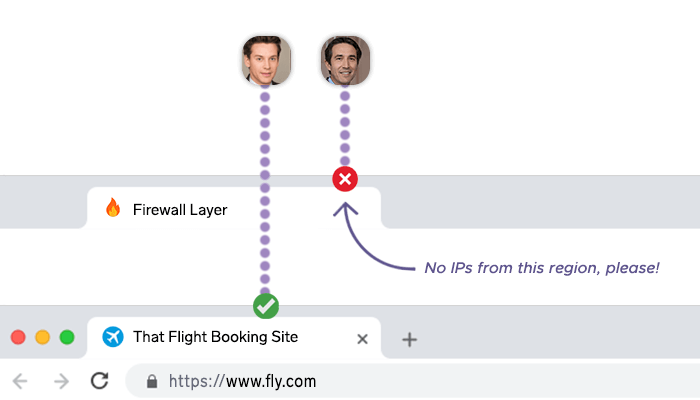
Firewalls operate by defining security rules that dictate what kind of traffic is permitted and what should be blocked. These rules can be based on various parameters, including:
- IP addresses: Restrict or allow traffic from specific IP addresses or IP ranges.
- Ports and protocols: Allow or block traffic based on the port number (e.g., HTTP on port 80) and the communication protocol (e.g., TCP or UDP).
- Traffic type: Filter traffic based on its type, such as web traffic, email, or file transfers.
- Packet content: Inspect the content of packets for potential threats, such as malware or viruses, often referred to as deep packet inspection (DPI).
Firewall Usage Scenarios
Firewalls are used in a variety of environments to secure networks. Some common usage scenarios include:
- Corporate networks: Businesses use firewalls to protect sensitive internal resources from external threats, prevent unauthorized access, and enforce corporate security policies.
- Home networks: Home routers often include built-in firewalls to protect personal devices, such as computers, smartphones, and smart home devices, from internet-based threats.
- Cloud environments: Firewalls are essential in cloud computing to protect virtual machines, storage, and data from unauthorized access, especially when dealing with multi-tenant environments.
- Data centers: Data centers rely on firewalls to safeguard large amounts of data, ensure secure communications between internal systems, and defend against DDoS attacks.
- Regulatory compliance: Organizations handling sensitive data, such as healthcare providers or financial institutions, may be required by law to implement firewalls to ensure data protection and comply with regulations like GDPR or HIPAA.
What Is a Proxy?
A proxy acts as an intermediary between a client and a server, facilitating requests and responses in the digital communication process. When a client (such as a user’s device or application) makes a request to access a resource on the internet, the request is routed through the proxy server. The proxy server retrieves the data from the target server and returns it to the client.
This intermediary role provides multiple benefits, including anonymity, security, performance enhancements, and controlled access to online resources.
How a Proxy Works
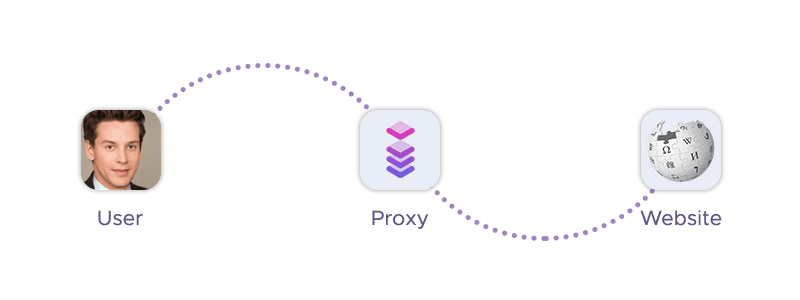
The basic workflow of a proxy can be summarized as follows:
- Client request: The client sends a request (e.g., to access a website) to the proxy server instead of directly contacting the target server.
- Request forwarding: The proxy server receives the client’s request, evaluates it, and then forwards it to the target server, often modifying or masking the original request to hide the client’s identity.
- Server response: The target server processes the request and sends the response back to the proxy server.
- Response delivery: The proxy server delivers the response to the client, sometimes altering it based on specific rules or configurations.
Proxy Types
Proxies operate at different layers of the network stack and can serve specific purposes based on their configuration and deployment. Here are some common types of proxies:
- Forward proxy: Sits between the client and the internet, acting on behalf of the client. Forward proxies are often used to enhance privacy, bypass geographical restrictions, or cache frequently accessed resources.
- Reverse proxy: Sits between the internet and a server, acting on behalf of the server. Reverse proxies are commonly used to distribute traffic, improve performance, and provide additional security for web servers.
- Transparent proxy: Intercepts requests without modifying them. Transparent proxies are often used for content filtering in corporate or educational environments.
- Anonymous proxy: Hides the client’s IP address from the target server, providing a degree of privacy.
- Residential proxy: Routes traffic through real devices with residential IP addresses, making the client appear as a regular user from a specific location.
- Datacenter proxy: Uses IP addresses assigned to data centers, providing high-speed access but less anonymity compared to residential proxies.
Proxy Usage Scenarios
Anonymity and privacy: Proxies help individuals and businesses mask their real IP addresses, ensuring privacy and reducing the risk of tracking or cyberattacks.
Content access and bypassing restrictions: Users can bypass geographical restrictions, censorship, or firewalls using proxies, enabling access to region-locked content or restricted websites.
Web scraping: Proxies are essential for web scraping, allowing automated bots to collect data from websites without being blocked or flagged.
Load balancing: Reverse proxies are used to distribute traffic across multiple servers, ensuring optimal resource utilization and preventing server overloads.
Content filtering: Organizations and schools use proxies to block access to certain websites or enforce acceptable use policies.
Enhanced security: Proxies can serve as a buffer against attacks by hiding the origin server or acting as a gatekeeper for incoming traffic.
Performance optimization: Caching proxies store copies of frequently accessed resources to reduce bandwidth usage and improve response times.
Comparison Table
| Aspect | Proxy | Firewall |
|---|---|---|
| Primary Purpose | Acts as an intermediary for client-server communication to enhance privacy, performance, or control. | Protects networks by monitoring and controlling incoming/outgoing traffic based on security rules. |
| Focus | Improves privacy, access control, and content delivery. | Secures the network against unauthorized access and cyber threats. |
| Operation Layer | Works primarily at the application layer (Layer 7) of the OSI model. | Operates at various layers, from network (Layer 3) to application (Layer 7). |
| Anonymity | Hides the client’s IP address and identity from target servers. | Does not focus on providing anonymity; instead, it safeguards the entire network. |
| Traffic Filtering | Filters requests based on IP, domain, or content type for specific purposes like access control. | Filters traffic based on security policies, including IP, port, and protocol-level rules. |
| Caching | Can cache web content to improve response times and reduce bandwidth usage. | Not designed for caching; focuses on inspecting and managing traffic in real-time. |
| Security Role | Provides basic security by masking IP addresses and enabling restricted access. | Ensures robust security by blocking malicious traffic, detecting intrusions, and enforcing policies. |
| Performance | Enhances performance through caching and load balancing (reverse proxy). | May introduce latency due to packet inspection, especially in deep packet inspection (DPI). |
| Common Use Cases | Web scraping; bypassing geoblocks or censorship; load balancing and performance optimization; enforcing acceptable use policies. | Network perimeter security; blocking unauthorized access to resources; preventing DDoS attacks; monitoring and logging traffic. |
| Deployment | Used in client-server setups to mediate requests. | Deployed at network entry/exit points to safeguard the entire network. |
| Types | Forward, reverse, transparent, residential, datacenter proxies. | Packet filtering, stateful inspection, proxy-based, next-generation firewalls (NGFW). |
| Key Strength | Improves user anonymity and provides access flexibility. | Protects against cyber threats and enforces network-wide security policies. |