While open proxies might seem like a convenient shortcut, they come with serious trade-offs. Their public nature makes them unreliable, slow, and often unsafe. In many cases, users of open proxies unknowingly expose themselves to malware, data theft, or legal risks – without ever realizing it. In this article, we’ll explain what open proxies are, why they’re risky, and how they compare to premium proxy solutions like Infatica.
What Is an Open Proxy?
An open proxy is a proxy server that’s freely accessible by anyone on the internet. It accepts connections from any user, without requiring authentication or limiting access – making it a tempting option for those seeking anonymity or a way to bypass geo-restrictions without paying.
At a basic level, a proxy acts as an intermediary between your device and the websites or services you’re accessing. Instead of connecting directly, your traffic is routed through the proxy, which hides your real IP address. Open proxies perform this same function – but without safeguards or access controls.
Users typically find open proxies on public proxy lists or forums, often posted without any information about who operates them or how they’re managed. And that’s part of the problem: when you use an open proxy, you’re trusting an unknown, unverified third party with your data – including everything from browsing activity to login credentials.
Key Differences Between Open and Paid Proxies
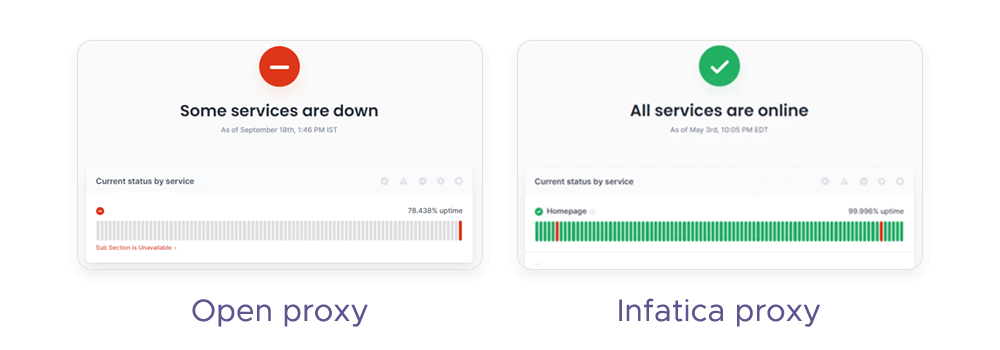
At a glance, open proxies and private proxies might seem to offer similar benefits – IP masking, access to geo-restricted content, anonymity. But when it comes to performance, security, reliability, and support, the differences are stark. Here’s a side-by-side breakdown:
| Feature | Open Proxy | Paid Proxy (e.g., Infatica) |
|---|---|---|
| Access Control | Open to everyone — no authentication required | Restricted to authorized users only |
| Speed & Stability | Often overloaded and slow | Optimized for speed, consistent uptime |
| Security | High risk of interception, data leaks, or malware | Encrypted, professionally managed, and regularly monitored |
| IP Reputation | Frequently blacklisted or flagged | Clean, rotating IPs with reputation management |
| Anonymity | May leak real IP or insert tracking scripts | Designed to maintain anonymity and data integrity |
| Legal Liability | Shared with anonymous users, often used for abuse | Legal compliance, clear ownership, transparent usage policies |
| Customer Support | None | Full technical support and onboarding assistance |
The Risks of Using Open Proxies

Open proxies may seem like a quick and easy way to gain anonymity online – but beneath the surface, they pose serious security, privacy, and legal risks. Let’s break down the most critical threats users face:
Security Vulnerabilities
When you use an open proxy, you have no control over who runs the server or how it handles your data. Many open proxies log traffic or actively intercept unencrypted data, including login credentials, session cookies, or personal information. Worse yet, some are deliberately configured to inject malware or redirect traffic to malicious sites.
Lack of Privacy
Despite their promise of anonymity, open proxies often do the opposite. Some are misconfigured and leak your original IP address, while others are operated by bad actors who monitor and record your activity. Without transparency or legal accountability, there's no way to know what’s being collected – or how it will be used.
Legal Liability
Open proxies are frequently used for illicit activities like spamming, credential stuffing, or scraping without authorization. Since they’re public, you share the IP address with unknown users – which means your activity could be flagged or traced alongside malicious traffic. In some cases, users of open proxies have been unwittingly associated with cybercrime investigations.
Unreliable Performance
Most open proxies are unstable and poorly maintained. They often suffer from high latency and slow speeds, limited bandwidth, and frequent downtime or deactivation without warning. For anyone doing serious work – like managing accounts, running bots, or performing data extraction – this unpredictability makes them unusable for production tasks.
Who Hosts These Proxies – And Why It Matters

One of the most overlooked dangers of using open proxies is not what they do, but who is behind them. Unlike paid proxy providers that offer transparency, infrastructure documentation, and legal accountability, open proxies are typically hosted by unknown third parties – and their motivations are rarely benign.
Compromised Devices Acting as Proxies
Many open proxies are not intentionally set up as public services – they’re hacked servers or infected machines. Cybercriminals exploit vulnerabilities in routers, misconfigured servers, or IoT devices and quietly repurpose them into proxy nodes. The original owners often have no idea their device is acting as a proxy – and users unknowingly participate in a larger botnet.
Malicious Operators and Honeypots
Some open proxies are set up deliberately by threat actors as honeypots – traps designed to lure in unsuspecting users. These proxies may:
- Log and sell your browsing data
- Steal credentials or tokens
- Inject malicious code into traffic
- Harvest personal or business intelligence for later exploitation
Because there's no vetting or support, there’s no recourse if something goes wrong.
No Transparency or Trust
With open proxies, there’s no way to verify:
- Who operates the proxy
- How your data is handled
- Whether the infrastructure is legal or safe
- Whether logs are stored or shared
When you rely on a proxy service, you’re trusting it with sensitive aspects of your online activity. Using an anonymous, unaudited server with no terms of service or compliance standards creates a black box of risk.
Why Paid Proxy Solutions Make a Difference
One of the key advantages of paid proxies is consistency. Unlike open proxies, which are often slow, unstable, or suddenly taken offline, premium proxy networks are built on robust, dedicated infrastructure. This means users benefit from reliable uptime, fast response times, and smooth connectivity – all of which are crucial for tasks like web scraping, automation, or managing multiple accounts.
Security is another critical differentiator. With open proxies, you never really know who’s operating the server or what’s happening to your data. In contrast, paid providers like Infatica offer transparent, professionally managed services that protect your traffic and privacy. You can trust that your data isn’t being logged, intercepted, or sold – and that the proxy you’re using is part of a secure and audited system.
Reputation also plays a major role. Open proxy IPs are often flagged or blacklisted due to abusive behavior from other users. This leads to frequent CAPTCHAs, blocked requests, and failed sessions. Paid proxy providers – especially those focused on business use cases – carefully maintain their IP pools to avoid these problems. With options like rotating residential IPs or clean datacenter proxies, users can operate at scale without being disrupted by poor reputation or access blocks.
Then there’s the matter of compliance and accountability. Free proxy services offer no guarantees or terms of use, and you have no recourse if something goes wrong. With a paid provider like Infatica, you know exactly who you're working with. There are clear usage policies, support channels, and infrastructure standards – all designed to ensure legal, ethical, and stable proxy usage.
And when something does go wrong, you’re not left on your own. Paid proxy services include technical support and customer service, helping users troubleshoot issues, fine-tune performance, or scale up their operations. Whether you need help integrating into an automation tool or configuring a large scraping project, you have experts on your side.