
Similar to IPs, MAC addresses play an important role in networking – however, their domain is internal, ensuring proper navigation between various devices in the given network. In this article, we’ll take a closer look at MAC addresses, learning how they work, why they get spoofed, and how to manage them.
What Is a MAC Address?
A MAC (Media Access Control) address is a unique identifier assigned to network interfaces for communication on a local network. It is a hardware address embedded into the network adapter (e.g., Ethernet or Wi-Fi card) by the manufacturer.
How a MAC Address Works
Uniqueness and assignment: MAC addresses are globally unique and assigned by the IEEE (Institute of Electrical and Electronics Engineers). Each manufacturer gets a block of MAC addresses to use.
Data transmission: When devices communicate over a local network (LAN), they use MAC addresses to identify each other. For example, when your computer sends data to a router, it uses the router’s MAC address.
OSI model layer: MAC addresses operate at Layer 2 (Data Link Layer) of the OSI model.
Unchangeable (mostly): MAC addresses are burned into hardware, but some devices allow changing them via software (MAC spoofing).
Role in security and filtering: Networks use MAC filtering to allow or block devices, and MAC addresses help track devices within local networks.
MAC Address Format:
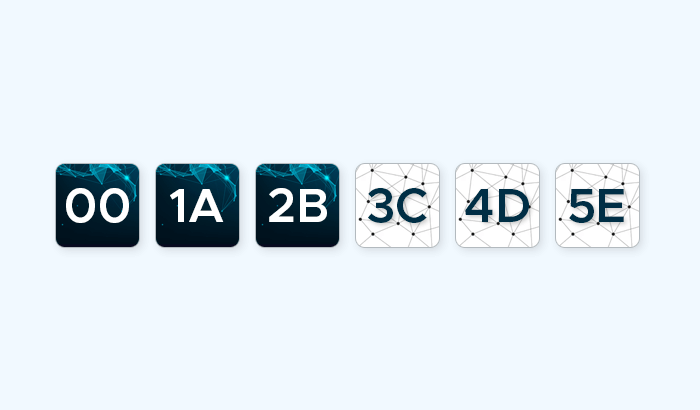
- A MAC address consists of 48 bits, usually represented as six pairs of hexadecimal digits (each pair separated by colons, hyphens, or no separators).
- Example:
00:1A:2B:3C:4D:5Eor00-1A-2B-3C-4D-5E. - The first 24 bits identify the manufacturer (Organizationally Unique Identifier, OUI), while the last 24 bits are unique to the device.
MAC vs. IP Addresses: Comparison Table
| Feature | MAC Address | IP Address |
|---|---|---|
| Definition | Unique identifier assigned to a network interface for local network communication. | Logical address assigned to a device for communication over a network (LAN or Internet). |
| Layer | Operates at Layer 2 (Data Link Layer) of the OSI model. | Operates at Layer 3 (Network Layer) of the OSI model. |
| Format | 48-bit address in hexadecimal (e.g., 00:1A:2B:3C:4D:5E). | 32-bit (IPv4, e.g., 192.168.1.1) or 128-bit (IPv6, e.g., 2001:db8::1). |
| Assignment | Assigned by device manufacturers and hardcoded into network interfaces. | Assigned dynamically by DHCP or manually by administrators. |
| Scope | Works within a local network (LAN). | Works across local and global networks (Internet). |
| Uniqueness | Globally unique (but can be spoofed). | Can change based on network location. |
| Purpose | Identifies a device on a LAN. | Routes packets across networks. |
| Example Use | Used by switches to forward data in a LAN. | Used by routers to determine packet destinations. |
How To Find The Mac Address On Different Systems
Windows
Using Command Prompt:
- Press
Win + R, typecmd, and press Enter. - Type the following command and press Enter:
ipconfig /all - Look for Physical Address under your active network adapter. For example,
00-1A-2B-3C-4D-5E.
Using Settings (GUI):
- Open Settings (
Win + I). - Go to Network and Internet > Wi-Fi or Ethernet.
- Click on your network and scroll down to find the Physical address (MAC).
MacOS
Using Terminal:
- Open Terminal (
Cmd + Space, typeTerminal, and press Enter). - Run this command:
ifconfig | grep ether - The MAC address will be listed next to ether, e.g.,
aa:bb:cc:dd:ee:ff.
Using System Preferences:
- Click on the Apple menu > System Settings.
- Select Network, then choose Wi-Fi or Ethernet.
- Click Details, and look for MAC Address.
Linux
- Open a terminal (
Ctrl + Alt + T). - Run this command:
ip link show. - The MAC address appears after
link/ether, e.g.,aa:bb:cc:dd:ee:ff.
Alternatively, run the ifconfig -a command and find the HWaddr field.
Android
Using Settings:
- Open Settings.
- Go to About phone > Status.
- Find Wi-Fi MAC address and Bluetooth MAC address.
Using Developer Options:
- Enable Developer Options by going to Settings > About phone and tapping
Build Number7 times until Developer Mode is enabled. - Open Developer Options and look for Hardware Addresses.
iOS (iPhone/iPad)
- Open Settings.
- Go to General > About.
- Scroll down to find Wi-Fi Address (this is the MAC address).
MAC Addresses Uses In Networking
Identifying Devices on a Local Network
Each device on a local area network has a unique MAC address, allowing network equipment like switches to identify and direct data to the correct recipient. For example:
- Your computer (MAC:
AA:BB:CC:DD:EE:FF) sends a file to a printer (MAC:11:22:33:44:55:66). - The switch in your network uses the MAC address to deliver the data to the correct device.
MAC Addresses and the OSI Model (Layer 2)
MAC addresses operate at Layer 2 (Data Link Layer) of the OSI model – think of an IP address as a street address (location-based) and a MAC address as a person’s name (unique per device). This means:
- They are used for local network communication.
- They help devices on the same subnet talk to each other without IP addresses.
How Switches Use MAC Addresses
Switches build a MAC address table (MAC forwarding table) to send data only to the intended recipient instead of broadcasting it to all devices. For example:
- Device A sends a packet to Device B.
- The switch learns Device A’s MAC and stores it in the MAC address table.
- The switch forwards the data directly to Device B instead of broadcasting to all devices.
- This reduces network congestion and improves efficiency.
MAC Addresses and ARP (Address Resolution Protocol)
Since MAC addresses work at Layer 2, and IP addresses work at Layer 3, they need a way to connect. ARP (Address Resolution Protocol) translates IP addresses into MAC addresses. For example:
- Your computer wants to send data to
192.168.1.100. - It sends an ARP request: “Who has 192.168.1.100?”
- The target device replies with its MAC address.
- Now, your computer knows which MAC address to send data to.
Wireless and Wired Network Usage
- Ethernet networks: Devices use MAC addresses to communicate over wired connections.
- Wi-Fi networks: Routers use MAC addresses to assign IP addresses via DHCP and route traffic.
For example, when you connect to Wi-Fi, the router assigns an IP address to your MAC address.
MAC Address Filtering and Security
Some networks use MAC address filtering to control access: Only devices with pre-approved MAC addresses can connect. However, this can be bypassed using MAC address spoofing.
MAC Address Randomization for Privacy
Modern devices (iOS, Android, Windows) randomize their MAC addresses when scanning for Wi-Fi networks to prevent tracking. This prevents public Wi-Fi networks from identifying and tracking you based on MAC addresses.
MAC Address Spoofing
MAC spoofing is a double-edged sword: It can enhance privacy or be used for malicious purposes. This is why organizations typically implement security measures to detect and prevent unauthorized MAC spoofing.
What is MAC Address Spoofing?
MAC spoofing is the practice of changing the MAC address of a device’s network interface (Wi-Fi or Ethernet) to another address. Here’s how it works:
- MAC addresses are normally hardcoded into network adapters.
- However, software tools can override this and make a device appear as if it has a different MAC address.
- This can be done manually via system settings or automatically using specialized tools.
Example commands for Windows (line 1) and Linux/macOS (line 2):
netsh interface set interface "Wi-Fi" newmac=00-11-22-33-44-55sudo ifconfig eth0 hw ether 00:11:22:33:44:55
Why is MAC Spoofing Used?
People spoof MAC addresses for various reasons – some ethical…
- Privacy and anonymity: Public Wi-Fi networks can track users via MAC addresses – and randomizing MAC addresses prevents tracking.
- Bypassing MAC-based restrictions: Some public Wi-Fi networks restrict access based on MAC addresses (e.g., only allow one device per user). Spoofing allows multiple devices to connect using the same account.
- Device testing and network administration: IT professionals and security researchers use MAC spoofing to test network configurations, security policies, and access controls.
- Fixing network connectivity issues: Some ISPs lock an IP address to a device’s MAC. If you change routers or adapters, spoofing the old MAC can restore internet access without calling the ISP.
… and some malicious – attackers often exploit it for their own purposes.
- Unauthorized network access via bypassing MAC filtering: Many networks use MAC address filtering to allow only approved devices – and a hacker can spoof an approved MAC to gain access.
- Unauthorized network access via stealing Wi-Fi access: Some ISPs and corporate networks bind MAC addresses to user accounts. Attackers can spoof a legitimate user’s MAC to use their network.
- Man-in-the-Middle (MITM) attacks via session hijacking: MAC spoofing can be used to impersonate a victim’s device. This tricks the router into sending the victim’s data to the attacker instead.
- Man-in-the-Middle (MITM) attacks via ARP spoofing: Attackers send fake ARP messages to associate their MAC address with another device’s IP address. This can redirect traffic through the attacker’s device, allowing packet sniffing and data theft.
- MAC address-based tracking and surveillance: Some companies, governments, and malicious actors track MAC addresses to monitor user behavior. Even if a device’s IP changes, its MAC remains the same, making tracking easier.
How to Protect Against MAC Spoofing Attacks
Organizations and individuals can take steps to detect and prevent MAC spoofing. Individuals can:
- Use randomized MAC addresses. Android and iOS support MAC address randomization to prevent tracking – enable it in Wi-Fi settings.
- Monitor your network: Use network monitoring tools like Wireshark to check for MAC address conflicts.
Organizations and network admins can:
- Use port security (MAC locking) on switches: Limits the number of MAC addresses per port, preventing unauthorized devices.
- Enable MAC spoofing detection: Some enterprise firewalls and switches detect if a device is sending packets with multiple MAC addresses.
- Use 802.1X authentication: Requires username and password authentication in addition to MAC addresses, making spoofing ineffective.
- Monitor for duplicate MAC addresses: If two devices claim the same MAC, it’s a red flag for MAC spoofing.
MAC Addresses and Proxies for Anonymity and Security
At first glance, MAC addresses might not seem relevant to proxy services, which primarily operate at the IP layer. However, they play a crucial role in network security, user tracking, and identity masking – key concerns for anyone using proxies for privacy, security, or business intelligence.
How MAC Addresses Affect Online Anonymity
When users connect to the internet, their MAC addresses are not exposed beyond their local network. Websites and online services cannot see them directly. However, MAC addresses can still compromise privacy in certain scenarios:
- Public Wi-Fi tracking: Many public networks log MAC addresses to track returning users, limit free sessions, or enforce security policies.
- Device fingerprinting: Some services use a combination of local MAC address data and other identifiers to recognize devices even if the IP address changes.
- ISP-level monitoring: Internet providers can associate a user's MAC address with their IP address, creating a persistent link between the user’s device and their online activity.
Proxies solve part of this problem by masking the IP address, but they do not change the MAC address itself. However, users who prioritize anonymity often combine proxy use with MAC randomization to prevent tracking across networks.
Why Proxy Providers Try To Prevent MAC Spoofing
While MAC addresses do not travel beyond a local network, they still play a role in the backend infrastructure of proxy services:
- Device authentication and access control: Many proxy providers implement access control mechanisms to prevent unauthorized use. Since MAC addresses are unique identifiers at the network level, some systems use them for internal authentication—though this approach is limited since MAC spoofing can easily bypass it.
- Residential proxy networks and ISP-level monitoring: Infatica’s residential proxies rely on real IP addresses assigned by ISPs, making them appear as legitimate user devices. Some ISPs monitor MAC addresses to enforce session limits, meaning proxy nodes might need to rotate not just IPs but also MAC addresses to remain undetected.
- Detecting and preventing proxy abuse: Some fraudulent users attempt to abuse proxy services by rotating IP addresses and using spoofed MAC addresses on their proxy nodes to bypass rate limits. Proxy providers need advanced traffic analysis and behavioral detection to prevent abuse while allowing legitimate users to maintain privacy.
- Enterprise and ethical hacking use cases: Some businesses and cybersecurity professionals use proxies alongside MAC spoofing for ethical penetration testing. For example, they might test whether a corporate network’s MAC filtering or IP blocking rules can be bypassed using both techniques together.