
In the early 2010s, a group of scientists from Stanford University, Massachusetts Institute of Technology, The Tor Project and SRI International came up with a research paper on evading internet censorship.
The researchers analyzed the circumvention methods and tools available at that time to create a new technique called flash proxy. Here is an outline of this approach.
Introduction
The internet was designed as a open network for data of any kind. However, nowadays, more and more countries and corporations are trying to filter traffic. Some censors block particular websites like Facebook or YouTube, while others restrict access to specific materials posted online. There are dozens of countries from all over the world, including Europe, using blocks of some kind on the internet.
Users in censored regions try to circumvent blocks using different methods, including proxies. There are several approaches to building such services, and Tor technology was used during this particular experiment.
Usually, developers on circumvention systems face three main challenges:
- Rendezvous protocols. A rendezvous protocol allows users in a censored region to send and receive a small amount of data to establish connections with a proxy. For example, Tor uses a rendezvous to distribute the IP-addresses of its bridges. Rendezvous protocols are used for low-rate traffic, so it is hard to block them.
- Proxy creation. Any circumvention system needs proxies outside of the region with the censored internet access to relay traffic between clients and target online resources. In turn, censors might try to prevent users from discovering the IP-addresses of these proxies and block these IPs. To stand against this Sybil attack, the circumvention system should be able to constantly create multiple new proxies. This is what the solution designed by the researchers aimed to do.
- Camouflage. When the client receives an IP address of a non-blocked proxy, they need to somehow hide this communication so that it is impossible to identify and block the session even using traffic analysis tools. This communication should be camouflaged to look like regular, allowed traffic in the form of a data exchange with an e-commerce website, or online game.
The researchers proposed a new approach to fast proxy creation.
How It Works
The key idea is to use a lot of websites to create multiple proxies with short lifespans, not exceeding a couple of minutes.
To implement this, a network of websites owned by volunteers (e.g., personal pages) is created.
NB: all of these websites are located outside of the censored region. These websites have no connection to the resources that clients want to access.
The owners of such websites install a special widget with a simple JavaScript-coded interface. Here is a sample code for the installation:
<iframe src="//crypto.stanford.edu/flashproxy/embed.html" width="80" height="15" frameborder="0" scrolling="no"></iframe>
Here is the widget:
When a web browser from a censored region gets to a website with an installed widget, it starts to relay traffic, i.e., the browser itself becomes a temporary proxy. When the user leaves the website, the proxy dies without a trace. As a result, this is sufficient enough to keep the Tor tunnel open.
To use the circumvention system, you need a Tor Relay, a web browser, and some additional elements. One of them is the facilitator that accepts requests from the client and connects them with a proxy. The communication goes via transport plugins (here is the Chrome Extension) and Tor-relay to switch from WebSockets to plain TCP.
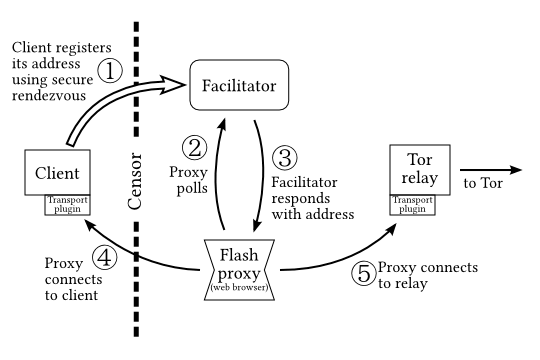
A typical session when using this system looks as follows:
- The client launches Tor, a flash proxy client (browser extension), and sends a registration request to a facilitator using the rendezvous protocol. The extension starts listening to the remote connection.
- The flash proxy goes online and sends the client connection request to the facilitator.
- The facilitator returns the registration and transmits the connection credentials to the flash proxy.
- The proxy connects to the client using the data from the previous step.
- The proxy connects to the transport plugin on Tor relay and starts a data exchange between the client and the relay.
The client never knows in advance where it will connect. The transport plugin accepts a fake destination address, which is needed only to comply with transport protocol requirements. This address is then ignored, and the tunnel to the other destination - a Tor Relay - is created.
Conclusion
The flash proxy project was in an active development stage for several years, but was discontinued in 2017. The project's source code is available here. There are now new censorship circumvention systems. One of them is the Snowflake project, which is built on the principles introduced in the flash proxy project.
Useful links and materials by Infatica:
- How Residential Proxies Are Useful For Businesses: Six Real Use Cases
- Research: Creating A Censorship-Resilient Proxy Tool Based On The Game Theory
- How to Catch When Proxies Lie: Network Proxy Service Location Verification Using An Active Geolocation Algorithm
Frequently Asked Questions
- HTTP proxies are the most common type. They allow you to browse the web anonymously by hiding your IP address.
- SOCKS proxies are more versatile than HTTP proxies. They can be used for both browser-based and client-based applications.
- VPNs provide the highest level of security. They create an encrypted tunnel between your device and the VPN server, preventing anyone from spying on your traffic or tampering with it.