Many teams that need to test, monitor, or verify web experiences run into strong edge protections like Cloudflare – and that can be confusing. Let’s analyze how modern protections work, why some requests get flagged, and how responsible use of proxies (for geo-testing, ad verification, QA and other permissioned tasks) can help teams generate realistic, auditable traffic without crossing legal or ethical lines.
How does Cloudflare work?
Cloudflare sits in front of a website and handles the traffic for it, acting like a smart front door. Instead of visitors going straight to the origin server, their requests hit Cloudflare’s global edge network first. That gives Cloudflare two big advantages: it can serve cached content quickly from an edge close to the user, and it can inspect and manage every request so the origin never has to deal with junk traffic or large attacks.
At a human level, Cloudflare does two things at once: it accelerates normal visitors and filters out trouble. For ordinary page loads it will try to return cached files from the nearest edge node so pages load faster. For anything that looks odd, the edge can slow the request down, challenge it, or drop it entirely – all before the origin ever sees it.
Technical fingerprints
Under the hood, Cloudflare combines a number of signals to decide what’s “odd.” It looks at how the TLS handshake was performed, the headers a browser sends, whether JavaScript runs in the expected way, timing patterns, and long-term reputation for the source IP. Those signals feed behavioral models and reputation databases; together they help tell apart a real person using a browser from an automated client that doesn’t behave like one. When the signals don’t add up, Cloudflare can require extra proof (a JavaScript challenge, rate-limited responses, or a CAPTCHA) or apply stricter rules that stop the request.
WAF
Cloudflare also includes a web application firewall (WAF) and configurable rulesets that stop clearly malicious things – SQL injections, cross-site scripting attempts, malformed requests, and other common attack patterns. Site owners can add custom rules on top of Cloudflare’s managed protections, which makes it possible to tune defenses for particular application quirks or threat models. Alongside the WAF, rate-limiting lets operators cap how many requests a single IP or session may make in a short time window, which is a simple but effective way to blunt scrapers or abusive crawlers.
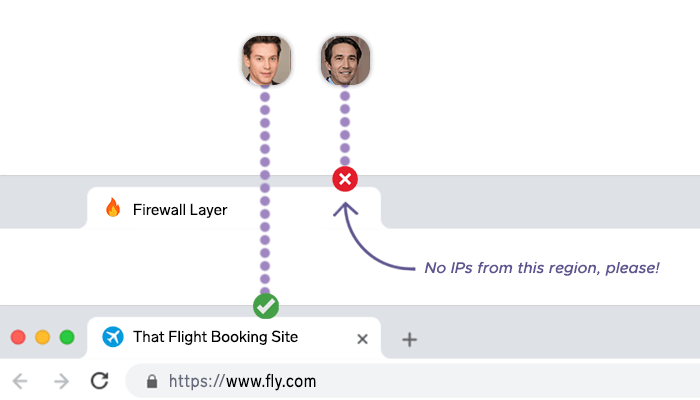
When an attacker tries to overwhelm a site with massive traffic (a DDoS), Cloudflare absorbs and filters that traffic across its worldwide network. Rather than one origin server being hammered, the load is diffused and suspicious flows are filtered away. Cloudflare can also block or challenge traffic by geography or by ASN (the network owner), which helps organizations exclude high-risk regions or network ranges when that fits their policy.
Do “Cloudflare solvers” work?
These are automated systems that attempt to handle the challenges Cloudflare presents to suspicious traffic. These challenges can include JavaScript checks, CAPTCHAs, or behavior tests that are easy for a real human and browser to solve, but difficult for a simple script or bot. A solver, in this context, is any tool or service designed to simulate what a real browser would do:
- Running the JavaScript Cloudflare injects to prove the client is a real browser.
- Passing cookies or session tokens back and forth correctly.
- Handling CAPTCHAs, sometimes by outsourcing them to human-based solving services.
Why Cloudflare challenges exist

Cloudflare’s detection systems look for signals that don’t match normal browsing – for instance, if the client doesn’t execute JavaScript, sends malformed headers, or makes requests too quickly. When the traffic looks unusual, Cloudflare responds with a challenge. The point is to separate real users from automated traffic before the request reaches the origin server. These mechanisms are constantly evolving, which is why tools built to “solve” them tend to be temporary.
How proxies can help you avoid Cloudflare checks
For teams that need to operate reliably and responsibly, there are safer, more stable alternatives. If your goal is quality assurance, geo-specific testing, or ad and content verification, residential proxies can be a great solution.

In everyday terms, a proxy is an intermediary for your requests. Rather than every outbound request coming from the same public IP on your server, it emerges from the IP address of the proxy. That simple fact supports several legitimate, non-evasive use cases that reduce the chance a request is mistaken for abuse.
Geography and realism
Many legitimate tasks require appearing to come from a particular country or region: QA teams need to confirm geo-specific content, advertisers need to validate regional creatives, and product teams need to see localized pricing or formats. Residential proxies are IP addresses assigned by real ISPs to home users, so requests coming from them usually carry the same network characteristics as ordinary consumer traffic.
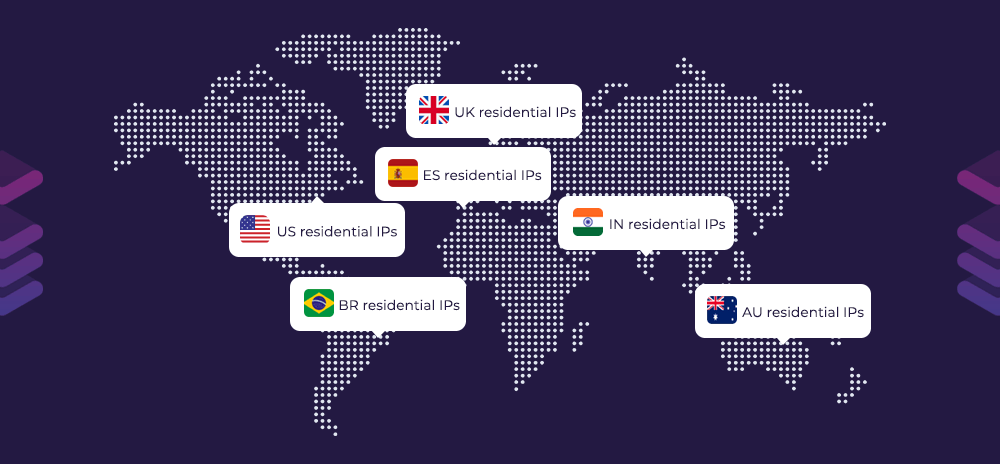
When a test or user journey genuinely originates from those regions, the traffic profile looks more “native” to the edge systems that evaluate it. That’s why, for testing and monitoring, residential proxies can reduce false positives compared with free proxies that look obviously automated or centralized.
Session persistence
Second, session persistence and IP diversity matter for benign workflows. If your automation or QA harness needs several persistent sessions or to test from a mix of locations, a proxy pool with session stickiness allows each test to keep a consistent IP for the length of the session. Conversely, having every test originate from one IP often trips simple rate limits or reputation checks. Distributing legitimate requests across well-managed proxy endpoints helps avoid triggering coarse protections that treat concentrated traffic as hostile – again, when you remain within acceptable request rates and follow site rules.
Finer control
Third, proxy providers often offer telemetry and controls – per-IP health checks, throughput limits, and usage logs. These tools help engineering teams instrument their traffic, spot anomalous patterns, and throttle back before they generate an incident or complaint. From a compliance standpoint, that observability is crucial: it makes testing auditable, helps show good faith if a site operator raises an issue, and supports cooperation (for example, enabling whitelisting for a known test pool).