- What Does a Proxy Server Mean?
- What Is a Proxy Server Used For?
- How Does a Proxy Server Work?
- Proxy Protocols
- Types Of Proxies
- Benefits Of a Proxy Server
- Proxy Server Risks
- Are Proxies Legal to Use?
- Are Proxy Servers Similar to VPNs?
- Where Do I Find Secure Proxy Servers?
- How Do I Set Up a Proxy Server?
- Frequently Asked Questions


Proxy servers can supercharge your online activities – but to use them efficiently, you need to understand them better. So what is a proxy server? In this comprehensive guide, you will learn what proxy servers are, how they work, what are their types, benefits, risks, and legal aspects, and how to set up a proxy server for your needs. You will also learn how to choose the best proxy provider, and why Infatica is a great option for your proxy needs.
What Does a Proxy Server Mean?
A proxy server acts as an intermediary between your device and the internet. It can modify or filter web requests and responses that pass through it, according to certain rules. For example, if you want to access a website that is blocked in your country, you can use a proxy server located in another country that can access the website. The server will send your request to the website and return the response to you, without revealing your own IP address. This way, you can bypass the geo-restriction and access the website.
What Is a Proxy Server Used For?
Proxy servers have many use cases, both for personal and business purposes. Here are some of the most common ones:
- Privacy: Hiding your real IP address and location from the websites you visit, making it harder for them to track you and collect your personal data. For example, if you want to browse the web anonymously, you can use a proxy server that masks your identity and protects your privacy.
- Security: Enhancing your security by filtering malicious web traffic and preventing cyberattacks. For example, if you want to protect your network from hackers, malware, or phishing, you can use a proxy server that scans and blocks harmful requests and responses.
- Load balancing: Distributing the workload among multiple servers, improving the performance and availability of websites and applications. For example, if you want to handle high traffic volumes and prevent server crashes, you can use a proxy server that balances the load and redirects the requests to the most suitable server.
- Site speed: Speeding up your web browsing by caching frequently accessed content and delivering it faster. For example, if you want to reduce the latency and bandwidth consumption of your website, you can use a proxy server that stores and serves the static files, such as images, videos, or scripts.
- Bypass censorship: Help you access geo-restricted or blocked content by routing your traffic through a different location. For example, if you want to watch a movie or a show that is not available in your country, you can use a proxy server that is located in a country where the content is accessible.
How Does a Proxy Server Work?
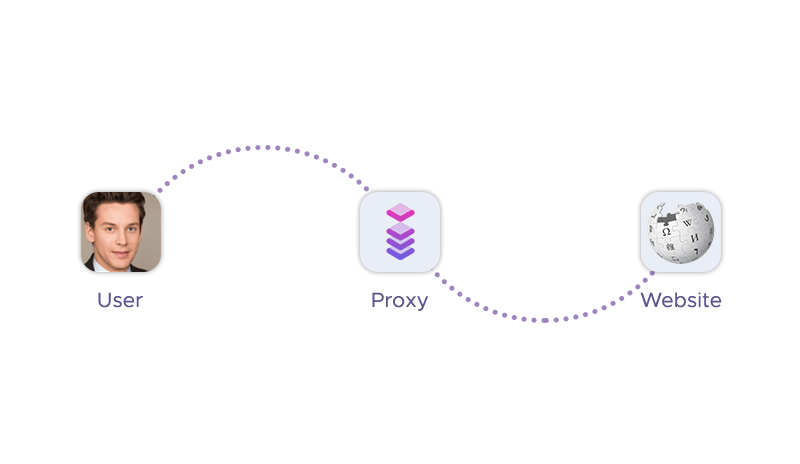
A proxy server works by intercepting the requests and responses that are sent and received by your device and the web server. Here is how it accomplishes that:
- When you enter a web address in your browser, your device sends a request to the proxy server, instead of a direct connection to the destination server.
- The proxy server checks the web request and decides whether to forward it to the web server or not, based on its rules. For example, it may block some requests that are harmful or inappropriate, or modify some requests to improve your speed or privacy. Otherwise, the proxy server forwards the requests.
- The destination server receives the request from the proxy server and processes it. It then sends a response back to the proxy server, which may also modify or filter the response according to its rules.
- The proxy server delivers the response to your device, which displays the web page in your browser. The web server does not know the user's real IP address, only the proxy server's IP address. This way, proxy servers act as a middleman between your device and the web server.
Proxy Protocols
Proxy protocols are network protocols that allow proxies to communicate with servers and clients without losing or altering the original information. However, proxies can also hide or modify the original IP addresses, hostnames, or protocols of the clients or servers, which can affect the functionality or accuracy of the applications. Proxy protocols solve this problem by adding headers that contain the original information to the TCP connections, so that the servers or clients can retrieve it. There are different types of proxy protocols, such as HTTP(S) and SOCKS.
HTTPS Proxy Server
HTTP(S) proxy protocol operates at the application layer of the OSI model. It is designed for HTTP and HTTPS protocols, which are used to access web pages and other web services. HTTP(S) proxy protocol adds headers that store the original IP address, hostname, and protocol of the client to the HTTP request. The server can read these headers and use them for various purposes, such as logging, authentication, or content delivery. HTTP(S) proxy protocol is widely supported by web browsers and web servers, and can also handle other protocols that use HTTP, such as FTP or WebSocket.
SOCKS Proxies
SOCKS proxy protocol operates at the session layer of the OSI model. It is designed for any TCP/IP protocol, such as SMTP, IMAP, FTP, or SSH. SOCKS proxy protocol establishes a TCP connection between the client and the proxy, and then relays the data between the client and the server. SOCKS proxy protocol does not add any headers to the data, but rather encapsulates the data in a SOCKS packet that contains the original IP address and port of the client. The server can read the SOCKS packet and use the information for various purposes, such as logging, authentication, or firewall rules. SOCKS proxy protocol is more versatile and secure than HTTP(S) proxy protocol, but also more complex and less supported by applications.
Types Of Proxies
There are different categories of proxies – and each has distinct features and functions. They all vary by the level of anonymity, protocol, IP address, or usage:
- Transparent proxies are proxies that do not hide the original IP address of the client. They are usually used by organizations or institutions to filter or monitor the internet traffic of their users. Transparent proxies can also cache web pages and save bandwidth.
- Forward proxies are proxies that act on behalf of the client. They are used by individual users to access the internet through a different IP address, location, or protocol. A forward proxy server can provide privacy, security, or content accessibility.
- Anonymous proxies are proxies that hide the original IP address of the client but reveal that proxy servers are being used. They are used by individual users to browse the web anonymously and protect their identity. An anonymous proxy server can also bypass geo-restrictions or censorship.
- Public proxies are proxies that are freely available on the internet for anyone to use. They are usually provided by volunteers or hackers who want to share their resources or disrupt the web. Public proxies can be fast and convenient, but also unreliable and risky.
- Shared proxies are proxies that are used by multiple users at the same time. They are usually provided by proxy providers who charge a fee for their proxy service. Shared proxies can be cheap and easy to use, but also slow and crowded.
- Rotating proxies are proxies that change the user's IP address after every request or at a certain interval. They are usually provided by proxy providers who have a large pool of IP addresses. Rotating proxies can be useful for web scraping, crawling, or automation.
- Reverse proxies are proxies that act on behalf of the server. Reverse proxy servers are used by organizations or websites to improve their performance, security, or availability. A reverse proxy server can also cache web pages, balance the load, or filter the incoming traffic.
- Residential proxies are proxies that use the IP address of a real device, such as a computer or a smartphone, that is connected to a residential network. They are usually provided by proxy providers who have agreements with internet service providers or users who share their IP address. A residential proxy can be very reliable and secure, but also expensive and slow.
- Mobile proxies are proxies that use the IP address of a real device, such as a smartphone or a tablet, that is connected to a mobile network. They are usually provided by proxy providers who have agreements with mobile carriers or users who share their IP address. Mobile proxies can be very authentic and undetectable, but also costly and limited.
- Datacenter proxies are proxies that use the IP address of a server that is located in a data center. They are usually provided by proxy servers providers who have access to a large number of IP addresses. Datacenter proxies can be very fast and cheap, but also detectable and blocked.
Benefits Of a Proxy Server
Proxy servers offer several benefits – here are some of them:
1. Enhanced Privacy and Anonymity

Proxies can enhance the privacy and anonymity of users by masking their real IP address and location from the websites they visit. This can prevent the websites from tracking them and collecting their personal data. For example, if a user wants to browse the web anonymously, they can use an anonymous proxy that hides their identity and protects their privacy.
2. Improved Security
Proxies can also improve the security of users, organizations, or websites by filtering malicious content and encrypting data transmission. This can protect them from cyberattacks, malware, phishing, or identity theft. For example, if a user wants to protect their network from hackers, they can use proxy servers that scan and block harmful requests and responses, or a proxy that uses HTTPS protocol to encrypt the data.
3. Access to Geo-Restricted Content
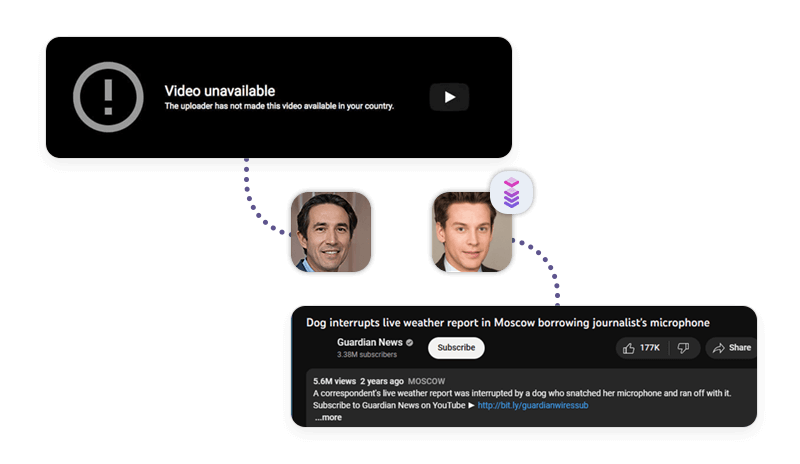
Proxies can enable users to bypass geographical restrictions and access content that is not available in their region. This can be useful for entertainment, education, or research purposes. For example, if a user wants to watch a movie or a show that is only available in another country, they can use a proxy server that is located in that country and access the content.
4. Bandwidth Savings and Faster Loading Times
Proxies can optimize the bandwidth usage and speed up the web browsing by caching frequently accessed content and delivering it faster. This can save bandwidth, reduce latency, and improve the user experience. For example, if a user wants to reduce the bandwidth consumption of their website, they can use proxy servers that store and serve the static files, such as images, videos, or scripts.
5. Network Performance and Load Balancing
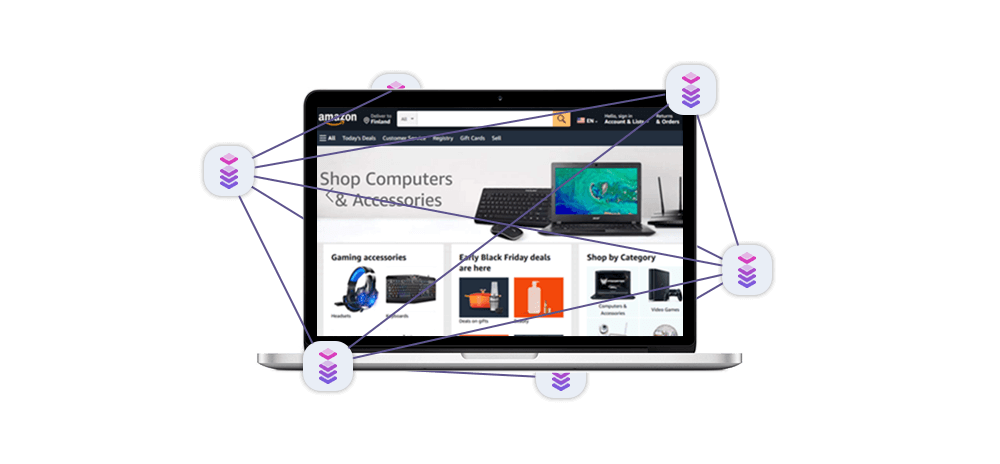
Proxies can improve the network performance and availability of websites and applications by distributing the traffic and load balancing among multiple servers. This can prevent server crashes, improve response time, and ensure reliability. For example, if a user wants to handle high traffic volumes and prevent server overload, they can use a proxy that balances the load and forwards requests to the most suitable server.
6. Content Filtering and Parental Controls
Proxies can also be used for creating web filters and setting up parental controls. This can be useful for organizations or parents who want to control internet usage of their employees or children. For example, if a user wants to block access to some websites or content that are harmful or inappropriate, they can use a proxy with a web filter for the requests and responses based on certain rules or keywords.
7. Secure Remote Access
Proxies can facilitate secure remote access to an internal network, especially in the context of VPN (virtual private network) proxies. VPN proxies are proxies that create a secure and encrypted tunnel between the client and the server, allowing the client to access the server's network as if they were physically there. For example, if a user wants to access their work network from home, they can use a VPN proxy that connects them to their work server and allows them to access the files, applications, or resources.
8. Efficient Data Monitoring and Logging
Proxies can assist in efficient data monitoring and logging for insights into internet usage. This can be useful for organizations or websites who want to analyze the traffic, behavior, or performance of their users or servers. For example, if a user wants to monitor the internet activity of their network, they can utilize proxy server logs to locate the requests and responses, and use them for compliance or security audits.
9. Cost Savings in Bandwidth Usage
Proxies can also contribute to cost savings by optimizing bandwidth usage, reducing server load, and minimizing data transmission costs. This can be beneficial for users, organizations, or websites who want to reduce their internet expenses and increase their efficiency. For example, if a user wants to save money on their internet bill, they can use a proxy servers that can cache web pages, balance the load, or compress the data.
Proxy Server Risks
You’ve just read the section detailing the proxies’ upsides – and you might be tempted to try a free proxy server, expecting the same benefits. Here are six reasons why regular proxy servers are a better choice:
1. Security Concerns
Free proxies can pose serious security risks to users who rely on them to protect their online activities. Untrustworthy proxies may intercept, modify, or steal the data that passes through them, such as passwords, credit card numbers, or personal information. Some proxies may also inject malware or viruses into the web pages or files that users download.
Furthermore, free proxies may not have proper security configurations, leaving users vulnerable to attacks from hackers or other malicious actors. For example, if a user uses a free proxy to access their bank account, proxy servers may capture their login credentials and use them for fraudulent purposes.
2. Privacy Risks
Free proxies can also compromise the privacy of users who use them to hide their identity or location. Many free proxies have unclear or shady logging policies, meaning they may record and store the users' IP addresses, browsing history, or other data. Some proxies may also share or sell this data to third parties, such as advertisers, marketers, or government agencies, without the users' consent or knowledge. For example, if a user uses a free proxy to visit a sensitive website, the proxy may log their activity and disclose it to someone who may use it against them.
3. Unreliable Performance
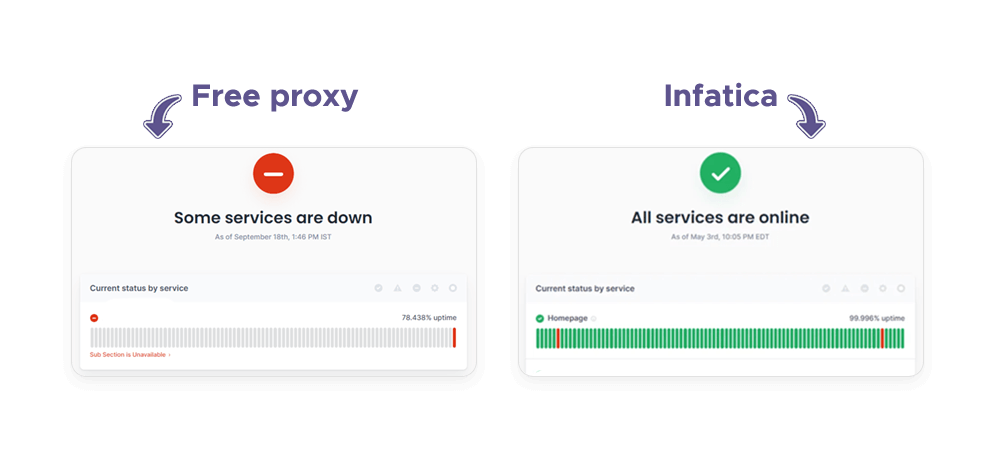
Free proxies can also affect the performance and reliability of users' internet connection. Due to the high demand and low supply of free proxies, users may experience slow connection speeds, frequent disconnections, or limited bandwidth. Some proxies may also have poor quality or outdated servers, which can cause errors, glitches, or crashes. For example, if a user uses a free proxy to stream a video, they may encounter buffering, lagging, or interruptions.
4. Lack of Transparency
A free proxy server can also be risky due to its lack of transparency and accountability. Users may not know who operates the proxy, where it is located, or what it does with their data. Some proxies may also have hidden or undisclosed features, such as adware, spyware, or backdoors, that can harm the users' devices or networks. For example, if a user uses a free proxy to download a file, they may unknowingly install a malicious program that can monitor their activity or damage their system.
5. Device and Network Compatibility Issues
Free proxies can also pose challenges for users who want to set them up on their devices or networks. Depending on the type, protocol, or configuration of the proxy, users may encounter compatibility issues that can affect the functionality or security of their devices or networks. For example, some proxies may not work with certain browsers, applications, or operating systems, or may require additional software or settings to work properly.
6. Data logging
Free proxies can also raise concerns about data logging, which is the practice of recording and storing the users' data that passes through the proxy. Data logging can infringe on the users' privacy and expose them to various threats, such as identity theft, blackmail, or legal action. Users may not be aware of or agree to the data logging policies of the proxy or may not be able to delete or access their data. For example, if a user uses a free proxy to send an email, the proxy may log their email address, content, or attachments, and use them for malicious or unethical purposes.
Are Proxies Legal to Use?
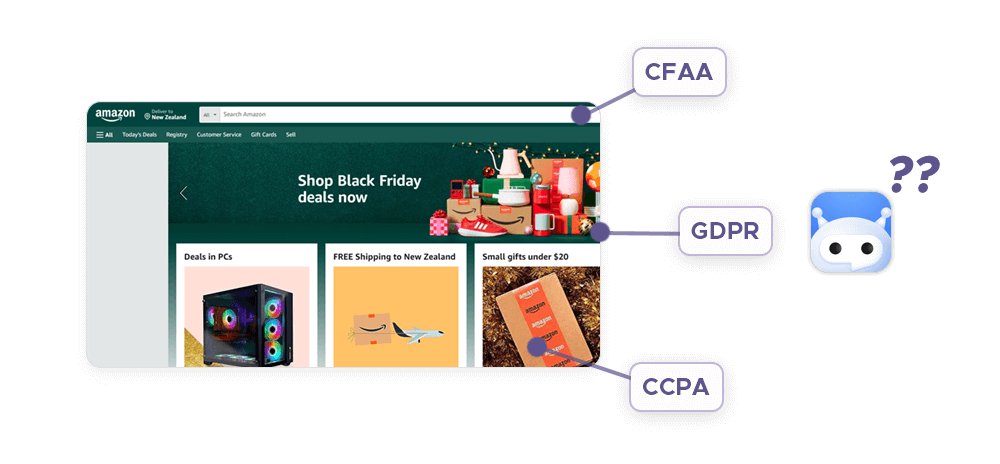
Proxies are legal to use in most countries, as long as they are used for lawful purposes and do not violate the terms of service of the websites or services that users access through them. However, proxies can also be associated with illegal or unethical activities, such as hacking, fraud, piracy, or censorship evasion. Therefore, users should be aware of the legal aspects of using a proxy server and exercise responsible usage within legal boundaries. Some of the potential legal concerns and guidance for using proxies are:
Terms of service and acceptable use
Users should comply with the terms of service and acceptable use policies of the websites or services that they access through proxies, and do not use proxies to violate or abuse them. For example, users should not use proxies to create multiple or fake accounts, spam, or manipulate online activities, such as voting, reviews, or ratings. Users should also avoid using proxies to access websites or services that are blocked or restricted by their network, employer, school, or government, as this may breach their contractual or legal obligations.
Proxies and ethics
Users should also consider the ethical and moral implications of using proxies, and do not use proxies to engage in or facilitate illegal or immoral activities, such as hacking, fraud, piracy, terrorism, or child exploitation. Users should also be aware of the potential harm or damage that their proxy usage may cause to themselves, others, or the society, and act accordingly.
Are Proxy Servers Similar to VPNs?

Virtual private networks are services that create a secure and encrypted tunnel between your device and a remote server, hiding your IP address and location. They work at the operating system level, meaning they affect all the traffic of your device, regardless of the app or browser. For example, if you use a VPN on your laptop, all the traffic from your laptop will be routed through the virtual private network, including the traffic from your browser, email client, or gaming app.
VPNs can be useful for more complex tasks, such as protecting your privacy, enhancing your security, or accessing geo-restricted content. They encrypt your data, meaning your traffic cannot be intercepted or monitored by anyone, even if you use a public Wi-Fi network.
Where do I find secure proxy servers?
Not all proxy providers are created equal, and choosing the best one for your needs can be challenging. To help you make an informed decision, here are some of the criteria that define a good proxy provider:
Proxy pool: size and quality
A good proxy provider should have a large and diverse pool of proxies, covering multiple locations, types, and protocols. This ensures that you can access any website or service you want, without facing IP bans, CAPTCHAs, or errors. Moreover, a good proxy provider should have high-quality proxies, meaning they are fast, reliable, and secure, and do not compromise your data or performance.
Infatica is a good example of a proxy provider that has a large and high-quality proxy pool, with over 15 million residential proxies, 5 million mobile proxies, and 5,000 datacenter proxies, covering over 150 countries and regions.
Pricing: flexibility and transparency
A good proxy provider should have flexible and transparent pricing plans, allowing you to choose the best option for your budget and usage. You should be able to pay only for what you use, and not be locked into long-term contracts or hidden fees. Moreover, a good proxy provider should have clear and honest pricing policies, disclosing all the details and features of their plans, and offering free trials or refunds if you are not satisfied.
Infatica is a good example of a proxy provider that has flexible and transparent proxy server pricing plans, offering pay-as-you-go, monthly, or annual plans, with unlimited traffic, IP rotation, and geolocation options, and providing a 3-day trial for $1.99.
Dashboard: usability and functionality
A good proxy provider should have a user-friendly and functional dashboard, allowing you to easily manage and monitor your proxies, and access various features and tools. You should be able to check your IP list, trigger rotation, change your geolocation, and more, with a few clicks. Moreover, a good proxy server should have a dashboard that integrates with other applications and services, such as web scrapers or anti-detection browsers, and supports various formats and protocols, such as HTTP, SOCKS, or API.
Infatica is a good example of a proxy provider that has a user-friendly and functional dashboard, offering a simple and intuitive interface, and supporting various integrations and formats.
How Do I Set Up A Proxy Server?
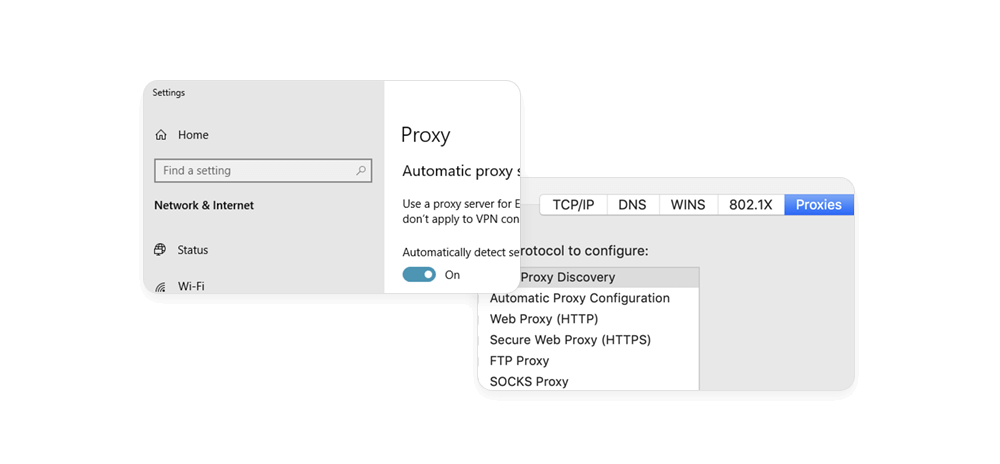
To set up a proxy server, you need to configure your device or browser to use the proxy server's address and port. Depending on your operating system, browser, or network settings, there are different ways to set up a proxy. Here are some of the common methods for Windows and Mac users:
Windows
Windows has a built-in proxy setting that allows you to set up a proxy server for your entire device. To access this setting, open the Settings app and click on Network & Internet. Then, click on the Proxy tab and choose from the list of available proxy settings. You can set up a proxy server automatically, using a setup script, or manually, by entering the proxy's IP address and port. Alternatively, you can also set up a proxy server for a specific browser, such as Chrome, Firefox, or Edge, by changing the browser's proxy settings.
macOS
macOS also has a built-in proxy setting that allows you to set up a proxy server for your entire device. To access this setting, open the System Preferences app and click on Network. Then, select the network connection that you want to use the proxy server for, such as Wi-Fi or Ethernet, and click on Advanced. Next, click on the Proxies tab and choose the type of proxy server that you want to use, such as Web Proxy (HTTP) or SOCKS Proxy. Then, enter the proxy server name or IP address and port, and click on OK. Similarly, you can also set up a proxy server for a specific browser, such as Safari, Chrome, or Firefox, by changing the browser's proxy settings.
Final Words
In this article, you have learned everything you need to know about the proxy technology, from the proxy server definition and functionality to their types and benefits, to their risks and legal aspects, to their setup and usage. You have learned the answer to the most important question: “What is a proxy server?” You have also learned how to choose the best proxy provider for your needs, and why Infatica is a reliable, secure, and transparent proxy service that offers a large and high-quality proxy pool, flexible and transparent pricing plans, and a user-friendly and functional dashboard. We hope that this article has helped you understand proxy servers better, and that you will use them responsibly and ethically.