Reverse proxy servers are an important tool for maintaining your online privacy, managing the networking infrastructure, and collecting data. But to use reverse proxies effectively, we need to understand their benefits, use cases, and configurations options. Let's do all of that in this article!
How does a reverse proxy server work?
A reverse proxy server works by intercepting client requests before they reach a backend server. When a client, such as a web browser, makes a request (e.g., to load a webpage), that request is first directed to the reverse proxy instead of the destination server. The reverse proxy then forwards the request to one of the backend servers, which could be selected based on various factors like load, proximity, or availability.
Once the backend server processes the request and generates a response (like the webpage content), it sends this response back to the reverse proxy. The reverse proxy then delivers the response to the client. Throughout this process, the client remains unaware of the actual backend server handling the request, as it interacts only with the reverse proxy.
Key functionalities of a reverse proxy
- Load balancing: Distributes incoming traffic across multiple servers to ensure no single server is overwhelmed, improving performance and reliability.
- Caching: Stores copies of frequently accessed content to serve future requests more quickly, reducing load on the backend servers.
- SSL termination: Handles encryption and decryption of SSL/TLS traffic, offloading this resource-intensive task from the backend servers.
- Security: Masks the IP addresses of backend servers, filtering malicious traffic, and preventing direct access to the servers.
Forward vs. reverse proxy servers
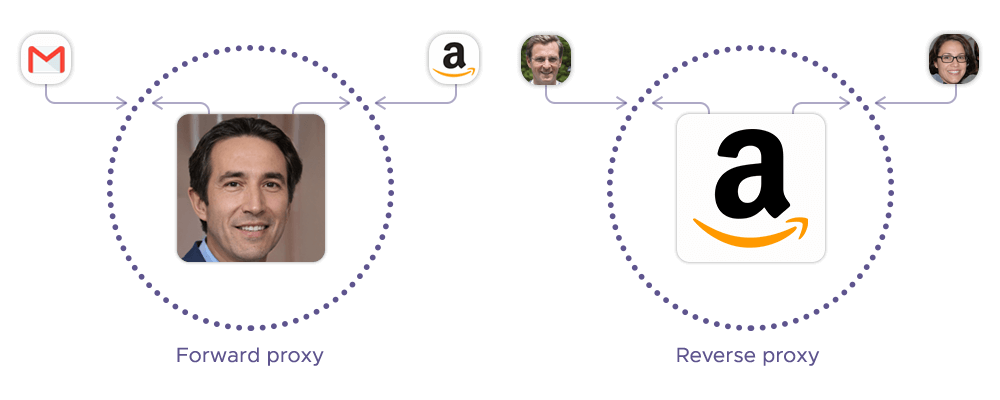
The term "reverse" in "reverse proxy" refers to the direction in which the proxy operates relative to traditional proxies, often called forward proxies. A forward proxy serves the client, acting as an intermediary that forwards the client's requests to external servers on the internet. It masks the client’s identity and can control or filter what the client can access. The flow is from client to proxy to server.
A reverse proxy, on the other hand, serves the server(s) rather than the client. It intercepts incoming requests from clients, forwards them to one or more backend servers, and then returns the server's response to the client. In this case, the flow is from client to reverse proxy to backend server.
| Feature/aspect | Forward proxy | Reverse proxy |
|---|---|---|
| Primary role | Acts on behalf of the client | Acts on behalf of the server(s) |
| Direction of traffic | Client → forward proxy → server | Client → reverse proxy → backend server(s) |
| Main purpose | Client anonymity, access control, content filtering | Load balancing, security, caching, SSL termination |
| Visibility | Hides the client’s IP from the server | Hides the server’s IP from the client |
| Common use cases | Accessing restricted content, bypassing geo-blocks, content filtering, anonymizing traffic | Load balancing, protecting backend servers, improving performance, managing SSL/TLS |
| User interaction | Users configure their devices to use a forward proxy | Users are typically unaware of the reverse proxy |
| Authentication | Can enforce user authentication before accessing external resources | Can manage authentication and access control for backend servers |
| Caching | Caches content from the internet for the client | Caches content from backend servers to serve clients faster |
| Security features | Controls access to certain websites, anonymizes browsing | Protects backend servers from direct exposure, mitigates DDoS attacks, enforces security policies |
| Examples | Web proxies, VPNs, corporate firewalls | Content Delivery Networks (CDNs), load balancers, web application firewalls (WAFs) |
| Impact on server | Minimal direct impact on server performance | Significant impact on distributing and managing server load and performance |
Business use cases of reverse proxy servers
Reverse proxies are versatile tools with several business use cases that enhance security, performance, and manageability. Here are some common scenarios where businesses leverage reverse proxies:
1. Load balancing: In high-traffic environments, reverse proxies distribute incoming requests across multiple servers to prevent any single server from becoming overloaded. This ensures that resources are utilized efficiently, improves response times, and enhances the overall availability and reliability of the service.
2. Security and DDoS mitigation: Reverse proxies act as a shield between the internet and backend servers, masking their IP addresses and protecting them from direct attacks. They can filter out malicious traffic, block Distributed Denial of Service (DDoS) attacks, and provide an additional layer of security by enforcing access controls and security policies.
3. SSL termination: Managing SSL/TLS encryption can be resource-intensive for backend servers. A reverse proxy can handle SSL termination, decrypting incoming requests and encrypting outgoing responses. This offloads the computational burden from the backend servers, enabling them to focus on processing requests and improving overall performance.
4. Caching and content delivery: Reverse proxies can cache static content, such as images, scripts, and style sheets, closer to users. By serving cached content for repeat requests, they reduce the load on backend servers and speed up response times. This is particularly beneficial for websites with high traffic or globally distributed users.
5. Global Server Load Balancing (GSLB): For businesses operating across multiple geographic locations, reverse proxies can be used to route user requests to the nearest or least-loaded server, optimizing performance and reducing latency. This setup is crucial for global applications, ensuring users receive fast and reliable access no matter where they are.
6. Application firewall: Reverse proxies can integrate with Web Application Firewalls (WAFs) to inspect incoming traffic for malicious activities, such as SQL injection or cross-site scripting (XSS) attacks. This helps protect web applications from common vulnerabilities by blocking or sanitizing harmful requests before they reach the backend servers.
7. Microservices management: In microservices architectures, reverse proxies can route requests to the appropriate microservice based on URL paths, headers, or other criteria. This ensures efficient request handling, simplifies the deployment of microservices, and allows for seamless scaling and updates without disrupting the overall application.
8. Zero downtime deployments: Reverse proxies can facilitate zero-downtime deployments by directing traffic to different versions of an application. During an update, a reverse proxy can gradually shift traffic from the old version to the new one, allowing businesses to deploy updates without interrupting service.
9. Authentication and Single Sign-On (SSO): Reverse proxies can handle authentication and authorization, including integrating with Single Sign-On (SSO) systems. This centralizes user authentication, simplifies access management, and enhances security by ensuring consistent enforcement of access controls across all backend services.
10. Legacy system integration: For businesses with legacy systems that cannot be easily upgraded, reverse proxies can act as a bridge, allowing new services to interface with older systems. They can translate modern protocols and requests into formats that the legacy systems can handle, extending the life of older infrastructure while enabling new functionality.
Pros and cons of reverse proxy servers
Reverse proxies offer significant benefits in terms of security, performance, and scalability, making them essential for many modern web applications and services. However, they also introduce complexity, potential single points of failure, and additional resource requirements, which need to be carefully managed to maximize their effectiveness.
Pros of reverse proxies
Enhanced security: By acting as an intermediary between the client and backend servers, reverse proxies hide the IP addresses of the servers, making them less vulnerable to direct attacks. They can also filter traffic, block malicious requests, and provide an additional layer of security, such as SSL termination and web application firewall (WAF) integration.
Caching: Reverse proxies can cache frequently requested content, reducing the load on backend servers and speeding up response times for users. This is particularly useful for static content like images, scripts, and stylesheets.
High availability: By distributing traffic and providing failover capabilities, reverse proxies help ensure that services remain available even if one or more backend servers go down. They can automatically route traffic to healthy servers, minimizing downtime.
Centralized authentication: Reverse proxies can manage user authentication and enforce access controls for all backend services. This centralization simplifies user management and enhances security by ensuring consistent enforcement of policies across different services.
Simplified maintenance and upgrades: Reverse proxies allow for seamless updates and maintenance of backend servers. Traffic can be routed to other servers during maintenance, enabling zero-downtime deployments and reducing the risk of service interruptions.
Cons of reverse proxies
Single point of failure: If the reverse proxy itself fails, it can take down access to all the backend servers it manages, leading to a complete service outage. This risk can be mitigated by implementing redundancy and failover mechanisms.
Complexity: Implementing a reverse proxy introduces additional layers of complexity into the network infrastructure. It requires careful configuration and management to ensure it operates effectively and securely. Misconfigurations can lead to security vulnerabilities or performance issues.
Latency: Reverse proxies add an extra hop between the client and the backend server, which can introduce some latency. While often negligible, it can be a concern in performance-critical applications, particularly if the reverse proxy is not optimally configured.
Resource intensive: Running a reverse proxy requires computing resources, especially when handling tasks like SSL termination, caching, and load balancing. This can lead to higher infrastructure costs and the need for more powerful hardware or virtual machines.
Maintenance overhead: Reverse proxies require ongoing maintenance, including updates, security patches, and monitoring. This can increase operational overhead and require skilled personnel to manage the system effectively.
Potential bottlenecks: If not properly scaled, a reverse proxy can become a bottleneck, limiting the performance of the entire system. This can happen if the proxy server is overwhelmed by traffic or if its resources are insufficient to handle the load.
Compatibility issues: Some applications or services may not be fully compatible with reverse proxies, requiring additional configuration or even custom solutions. This can complicate the deployment process and lead to unexpected issues.
Reverse proxies' parameters that can be modified
Reverse proxies are highly configurable, allowing you to modify various parameters to tailor their behavior to specific needs. Here are some of the key parameters that can be modified:
| Feature | Description | Settings |
|---|---|---|
| Load balancing algorithms | You can choose from various algorithms to determine how traffic is distributed among backend servers. | Round robin: Distributes requests sequentially across all servers. Least connections: Directs traffic to the server with the fewest active connections. IP hash: Routes requests based on the client’s IP address, ensuring the same client consistently reaches the same server.Weighted: Assigns different weights to servers based on their capacity, directing more traffic to more powerful servers. |
| Caching policies | Caching parameters control how the reverse proxy stores and serves cached content. | Cache expiration: Defines how long content is cached before it’s refreshed. Cache size: Limits the total amount of data stored in the cache.Cache bypass rules: Specifies conditions under which content should not be cached (e.g., dynamic pages, user-specific content). |
| SSL/TLS configuration | SSL/TLS parameters control how the reverse proxy handles encrypted traffic. |
SSL termination: Enables the reverse proxy to decrypt incoming SSL/TLS traffic.
Certificate management: Allows for the configuration of SSL certificates, including automated renewal with services like Let’s Encrypt.
Cipher suites: Specifies which encryption algorithms are supported for secure connections.
SSL offloading: Offloads the SSL processing from backend servers to the proxy.
|
| Security features | Various security settings can be configured to protect backend servers and data. | IP whitelisting/blacklisting: Controls which IP addresses are allowed or blocked from accessing backend servers. Rate limiting: Limits the number of requests a client can make in a given time frame to prevent abuse or DDoS attacks. Web application firewall rules: Configures rules for blocking common attack vectors like SQL injection or cross-site scripting (XSS).Access control lists (ACLs): Defines who can access specific resources based on user roles or IP addresses. |
| Timeout settings | Timeout parameters control how long the reverse proxy waits for certain events before terminating a connection. | Client timeout: How long the proxy waits for the client to send a request. Server timeout: How long the proxy waits for the backend server to respond.Connection timeout: The duration before a connection attempt to a backend server is considered failed. |
| Session persistence (Sticky Sessions) | Configurable session persistence ensures that a client’s requests are consistently routed to the same backend server. | Cookie-based persistence: Uses cookies to maintain the session with a specific server. IP-based persistence: Keeps the client connected to the same server based on their IP address.Session timeout: Determines how long a session remains sticky before expiring. |