
Fake IP generators promise quick anonymity and effortless IP changes, but most rely on simple tricks that don’t actually mask your identity or protect your data. In reality, they introduce significant security risks and fail in nearly every real-world use case. Let’s explore how these tools work, why they’re unreliable, and which safe, legitimate IP solutions businesses should use instead.
What Are Fake IP Generators?
Fake IP generators are online tools or browser extensions that promise to “mask” your real IP address by assigning a random or fabricated one. They typically target users who want quick anonymity, access to geo-restricted content, or a simple workaround for basic website restrictions. While the name suggests they can create a fully functional new identity on the internet, the reality is far more limited.

Most fake IP generators don’t provide a real, routable IP address. Instead, they display an arbitrary number sequence to give the illusion of IP spoofing – without changing the underlying network connection. Some offer a lightweight proxy or web-based redirection layer, but even these lack proper infrastructure, secure routing, or legitimate IP sourcing. Unlike true proxy networks, these tools do not manage sessions, maintain stable connectivity, or ensure compatibility with modern websites.
Why Fake IP Generators Don’t Actually Work
Despite promising a fast and effortless way to “change” your IP address, fake IP generators cannot deliver functional anonymity or reliable identity masking. Their core limitation is technical: modern internet communication requires two-way, fully routable traffic, which can’t be achieved by simply displaying a fake IP on the user’s device.
At the network level, websites expect real, verifiable signals such as Autonomous System Number (ASN), geolocation metadata, reverse DNS records, and proper handshake behavior. Fake IP generators cannot supply any of these because they do not control an actual network or IP subnet. As a result, websites detect them instantly – whether through mismatched IP headers, missing infrastructure data, or clear inconsistencies in the network path.
Even the versions that claim to “spoof” packets fail in practice. IP spoofing only works for one-directional traffic, which is incompatible with HTTPS, login flows, verifications, and virtually all modern web interactions. For tasks such as scraping, automation, or geo-testing, fake IP generators collapse immediately: requests time out, sessions break, and blocks occur almost instantly.
Security & Privacy Risks of Fake IP Generators

Beyond their technical limitations, fake IP generators carry serious security and privacy risks – often far greater than users anticipate. Because these tools operate outside any established network, compliance framework, or infrastructure standard, they expose users to threats that legitimate proxy or VPN providers actively work to mitigate.
Many fake IP generators are distributed through unverified websites, freeware portals, or suspicious browser extensions. These sources frequently bundle malware or spyware designed to harvest browsing activity, login credentials, cookies, or session tokens. Once installed, such tools can monitor traffic, inject ads, or perform man-in-the-middle attacks without the user’s awareness.
A significant concern is the lack of encrypted routing. Since these generators don’t manage real IP networks, they often send data through unprotected channels or through unknown third-party servers. This creates a direct risk of interception – especially when users attempt to log into accounts, perform financial transactions, or scrape business-critical data.
For organizations, the consequences are even more severe. Using such tools can lead to credential leaks, compromised internal systems, blacklisting of corporate IP ranges, and violations of data protection or compliance requirements. What begins as an attempt to “quickly change an IP” can escalate into tangible legal, operational, and reputational damage.
Use Cases Where Users Think Fake IPs Work – and Why They Fail
Many users turn to fake IP generators for tasks that legitimately require IP masking – but these tools consistently fall short because they don’t provide real, routable, or trustworthy network identities.
Web Scraping & Crawling
Scraping platforms quickly detect non-routable or inconsistent IP metadata. Fake IPs lack proper ASN, geolocation, and reverse DNS data, causing websites to block requests instantly. As a result, scripts break, data pipelines fail, and scraping jobs return incomplete or empty results.
Market & Price Research
Businesses often test region-specific pricing or content. Fake IP generators cannot provide real geolocation targeting; they only pretend to. The websites still see the user’s original IP, leading to inaccurate data and unreliable market insights.
Ad Verification
Ad networks require clean, legitimate, residential or mobile IPs to validate impressions. Fake IP generators trigger fraud-detection systems since they do not originate from trusted networks. Verification attempts are rejected, and the data becomes useless.
Automation & Account Management
Platforms such as social networks, e-commerce sites, and SaaS tools monitor IP consistency and session behavior. Fake IPs cannot maintain stable sessions or produce valid traffic signals. Login flows break, accounts get flagged, and automated tasks fail to execute.
Geo-Restricted Content Checks
Users try fake IPs to access location-specific content or website versions. Because no real IP change occurs, these attempts simply do not work. Services identify the true location immediately and continue to block or redirect traffic.
How to Choose a Safe Alternative to Fake IP Generators
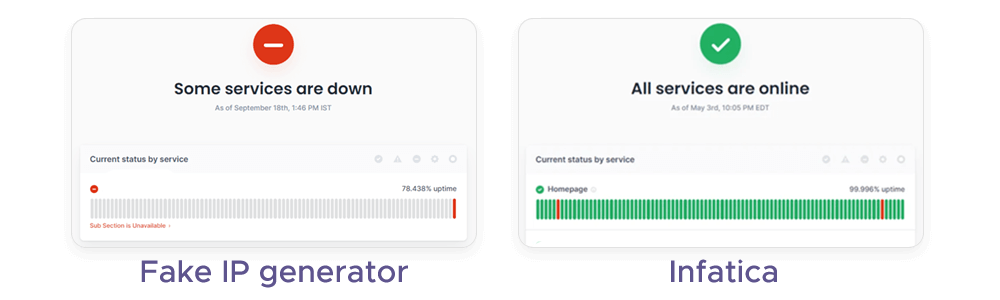
When selecting an IP solution for privacy, data collection, or geo-specific tasks, you should evaluate whether the provider offers reliable, secure, and legitimate infrastructure. A trustworthy solution should answer “Yes” to every question – and Infatica’s proxy ecosystem is designed to meet all of them.
Is the IP source legitimate and ethically acquired?
Real privacy and compliance start with real IPs. Reliable networks use properly sourced residential, datacenter, ISP, and mobile IP addresses – not fabricated or recycled ones.
🔍 Infatica's IPs come from verified, compliant sources.
Does the provider offer secure, encrypted traffic routing?
Encryption ensures that no third party can intercept credentials, session data, or sensitive business information.
🔍 Infatica routes traffic through secure, encrypted channels.
Can you select real geolocations – countries, cities, or ASN types?
Accurate geo-targeting is crucial for market research, scraping, ad verification, and QA testing.
🔍 Infatica's clients can choose from 195+ geolocations and several IP types.
Does the solution support stable sessions, rotation control, and long-term reliability?
Business-critical workflows require uninterrupted sessions, flexible rotation settings, and consistent performance.
🔍 Infatica supports session control, rotation modes, and dedicated resources are built in.
Is the proxy network backed by real support, monitoring, and uptime guarantees?
Quality providers ensure uptime, performance consistency, and responsive technical support – not anonymity tricks.
🔍 Infatica offers SLAs, monitoring, and 24/7 support ensure dependable operation.