- What are SOCKS Proxies and How do they work?
- Advantages and Disadvantages of SOCKS Proxies
- What are HTTP Proxies and How do they work?
- Why use HTTP Proxies?
- Advantages and Disadvantages of HTTP Proxies
- Why do proxies need ports?
- SOCKS vs. HTTP Proxy Comparison Table
- Why you should choose Infatica as your proxy provider
- How to set up proxy manually
- Frequently Asked Questions


What is a SOCKS proxy? How does it stack up against its counterpart, the HTTP proxy? The differences between the two proxies and their basic functionality is important to get right if you want to set up an efficient data collection pipeline – and you need a good understanding of how SOCKS proxy works for that.
In this article, we’re pitting the SOCKS vs. HTTP solutions against each other, exploring the technologies behind the SOCKS and HTTP protocols, their differences, reasons to use each type of proxy, how to set them up, how to use a SOCKS proxy, and more.
What are SOCKS Proxies and How do they work?
Let’s start with a more general question: What is a SOCKS protocol? SOCKS (short for Socket Secure) is a network protocol for transferring data to the server. SOCKS functions on behalf of its user when it sends packets through a firewall via routing traffic of the user to the destination server. To do this, SOCKS uses the Transmission Control Protocol (TCP). It establishes a TCP connection to the destination server and starts the exchange of data packets between the user and the server.
A major advantage of the SOCKS protocol is its versatility: It can route all types of network traffic created by all types of software or protocols. This makes SOCKS proxies the go-to solution for heavy-duty processes like streaming and peer-to-peer sharing. An added benefit is better anonymity: proxies change the user’s IP address, which can be used to circumvent geolocation-based restrictions.
Naturally, Infatica’s proxy solutions support the SOCKS protocol, which means you can use them for any application or protocol that requires a secure and anonymous connection.
What are SOCKS4 Proxies?
SOCKS4 is an older protocol that provides basic proxy functionality but lacks support for advanced features like authentication and the UDP protocol. It can only handle TCP connections and IPv4 addresses. A SOCKS4 proxy server accepts incoming client connection requests on TCP port 1080 and relays them to the desired destination.
What are SOCKS5 Proxies?
SOCKS5 is a newer protocol that extends the SOCKS4 model to include UDP, IPv6, and various authentication methods. A SOCKS5 proxy server can also perform DNS lookups on behalf of the client. SOCKS5 offers more security and flexibility than SOCKS4.
What differentiates SOCKS4 from SOCKS5?
This protocol features two versions: SOCKS4 and SOCKS5 – this is where the SOCKS5 meaning comes from. Their main points of differences are:
- Authentication: SOCKS5 can use several authentication methods, while SOCKS4 doesn’t support authentication at all.
- UDP proxies: SOCKS5 supports them, SOCKS4 doesn’t.
- Security: SOCKS5 offers better security thanks to routing traffic via a more complete TCP connection and SSH tunneling methodology.
In practice, the terms “SOCKS” and “SOCKS5” are used interchangeably: The protocol’s 5th version is more popular and feature-complete, so it’s common to drop the “5” altogether when talking about SOCKS.
Advantages and Disadvantages of SOCKS Proxies

In some scenarios, using a SOCKS proxy is the optimal choice thanks to its structure-specific features and benefits. Let’s take a closer look at what it can offer:
Advantage 1. Gets you around internet blocks
Acting as a middleman between you and the destination server, a SOCKS5 proxy improves your anonymity, making it impossible for third parties to see your real IP address. If a streaming service, for instance, is cordoned-off from users with European IP addresses, you can circumvent this restriction.
Advantage 2. Faster and more reliable connection
We mentioned that SOCKS uses Transmission Control Protocol (TCP), an advanced data transfer protocol – but it also supports User Datagram Protocol (UDP) as an alternative. The TCP protocol is rather rigid when it comes to sending data, designed to follow a strict order of network packets and merge them into a stream. UDP, on the other hand, is more flexible and offers a faster and more reliable internet connection – and this advantage is extended to SOCKS servers as a whole.
Advantage 3. Fewer errors and improved overall performance
Unlike other proxy types, SOCKS proxies don’t modify the headers of data packets. This is beneficial for performance as the proxy has less heavy-lifting to do and doesn’t risk misrouting traffic. Still, there is a downside to unedited headers: They contain the user’s personal information – if intercepted, they may make it easier to determine where these data packets came from.
Advantage 4. Better performance on P2P platforms
SOCKS is optimized for sending smaller data packets, which makes it the optimal choice for saving data from the web. Offering faster download speeds, it’s well-suited for low-latency tasks and peer-to-peer sharing websites and apps, with torrent software as a typical example.
However, this proxy type isn’t without its downsides:
Disadvantage 1. Lack of encryption
One of the biggest flaws of a SOCKS proxy is the lack of encryption. If someone uses a protocol that doesn't use encryption, an intruder can look at the data as it leaves the computer for the server. For this reason, you never want to use public Wi-Fi hotspots to conduct private business with a SOCKS5 proxy.
Disadvantage 2. Limited compatibility
SOCKS proxies are not compatible with all applications and protocols. Some applications may not support them at all, or may require additional configuration to work properly. For example, some web browsers may not be able to handle HTTPS traffic through a SOCKS proxy. This can limit the functionality and security of your online activities.
Disadvantage 3. Higher cost
SOCKS proxies are usually more expensive as they offer more features and flexibility. However, this also means that they consume more bandwidth and resources, which can affect your network performance and speed. If you are looking for a cheap and simple way to hide your IP address, a SOCKS5 proxy may not be the best option for you.
What are HTTP Proxies and How do they work?
Just like SOCKS, the HyperText Transfer Protocol (HTTP) is another protocol for transferring data across the web. The end result of using this proxy type is the same: you get a new IP address – but the technology behind the HTTP proxy servers is different.
HTTP proxies are engineered for a higher abstraction level compared to their SOCKS counterparts: The latter have more low-level access to network components, making them more secure; the former can analyze web traffic, which makes HTTP proxies better suited to collect data. Using a HTTP-based proxy, web scraping software can differentiate between relevant and irrelevant data.
HTTPS proxies
HTTPS is a variation of HTTP, with S for “Secure”. As the name suggests, the HTTPS protocol provides a more secure network environment via end-to-end encryption. This makes HTTPS proxies the optimal tool for sending sensitive data – a good example is connecting to your bank’s website or using an intranet.
Why use HTTP Proxies?

HTTP proxies are intermediaries that forward requests and responses between the client and the server. They can be used for various purposes, such as:
Web scraping
HTTP proxies can help web scrapers to extract data from websites without IP bans. By using proxies, web scrapers can change their IP address, avoid rate limits, bypass geo-restrictions, and access content from different locations.
Automation
HTTP proxies can enable automation tools to perform tasks on the web more efficiently and reliably. For example, proxies can help bots to create accounts, post comments, fill forms, click links, and perform other actions on websites without being detected or rejected.
Accessing geo-restricted content
HTTP proxies can help users to access content that is not available in their region or country: They’re allowing users to spoof their location and appear as if they are browsing from another place. For example, proxies can help users to watch streaming services, play online games, or use social media platforms that are blocked or restricted in their area1.
Data aggregation
HTTP proxies can help data aggregators to collect and analyze data from various sources on the web. By using proxies, data aggregators can overcome challenges such as IP blocking, captcha solving, bandwidth throttling, and data quality issues. For example, proxies can help data aggregators to monitor prices, track competitors, gather market intelligence, and generate insights.
Ad verification
This proxy type can help advertisers and publishers to verify the quality and performance of their online ads. By using proxies, ad verifiers can check if the ads are displayed correctly, reach the intended audience, comply with the regulations, and deliver the expected results. For example, proxies can help ad verifiers to detect fraud, measure impressions, test landing pages, and optimize campaigns.
Social media marketing
They can help social media marketers to manage multiple accounts, create engaging content, grow their followers, and increase their reach. By using proxies, social media marketers can avoid account suspension, bypass rate limits, target different markets, and automate their tasks. For example, proxies can help social media marketers to post updates, like comments, follow users, and send messages on various platforms.
Advantages and Disadvantages of HTTP Proxies
A HTTP proxy is versatile and powerful, offering a set of great features of its own. These include:
Advantage 1. Improved security
This proxy server type is able to deny suspicious data packets – this protects you against malware, spyware, and other forms of malicious content. The HTTPS variant provides an additional layer of security, which protects the data you’re sending with end-to-end encryption.
Advantage 2. Cleaner data
HTTP and HTTPS proxies have basic data analysis capabilities: In the area of web traffic transfer, they can be used to check for errors, filter content, and caching. Equipped with an HTTP proxy, your web scraper can parse the website’s target data without crawling irrelevant content.
Advantage 3. Easier data collection
This proxy server type can also modify HTTP request headers, which is crucial for maintaining high request success rate during data collection. Custom request headers enable your web scraper to circumvent websites’ restrictions – and be a less likely target for IP blocking overall.
However, there are some negative features associated with the HTTP and HTTPS solutions:
Disadvantage 1. Lower anonymity
They are less anonymous, as they can reveal more information about the client to web servers. Additionally, they can pass along the client’s IP address, browser type, cookies, and other data in the HTTP headers, unless they are modified or removed.
Disadvantage 2. Higher latency
HTTP/HTTPS proxies servers can cause higher latency than SOCKS proxies, as they have to process and interpret network traffic before forwarding it to the client. They can also add extra data packet headers and modify the content of the data, which can increase the size and complexity of the traffic.
Disadvantage 3. Lower reliability
They can be less reliable as they depend on the availability and performance of the web servers they connect to. Moreover, they can also encounter errors or failures when handling HTTPS traffic, as they may not be able to decrypt or encrypt it properly.
Why do proxies need ports?
Proxies feature several identifiers that make it possible to use them without mixing things up: the address (which is basically an IP address like 192.158. 1.38), the username/password combo for authentication, and the port. The last component is important because some types of proxies can only operate at a specific port.
SOCKS connection can be established with practically any port number (1080, 37192, etc.) Therefore, this option might be easier when there are network restrictions to consider – for instance, when some ports are blocked by the network administrator.
HTTP and HTTPS connections typically require a specific port to work properly: port number 443 for HTTPS and port number 80 for HTTP.
SOCKS vs. HTTP Proxy Comparison Table
Each of this proxy type was engineered for specific use cases, with one reigning supreme in security and the other dominating in performance. In the “HTTP proxy vs SOCKS proxy” debate, no proxy type is “better” – we just need to understand the scenarios where they excel.
| Criterion | SOCKS proxy | HTTP proxy |
|---|---|---|
| Anonymity and security | Designed to be private and secure, used around the world as a sound tool for bypassing government censorship. | May provide more security features thanks to their packet analysis, which can stop different types of malware penetration; HTTPS proxies also offer data encryption. |
| Functionality | Generally limited to its respective protocols. | More flexible thanks to their support of different network protocols. |
| Connection speed and performance | Designed for smaller data packets, which are typically found in P2P file sharing or uploading files to websites. | Can be configured to cache content, providing decent load speeds or providing additional support during web scraping. |
| Use cases | More versatile and can handle any type of internet protocol, such as HTTP, HTTPS, FTP, SMTP, and UDP. They are suitable for applications that require high-speed data transfer, such as video streaming, gaming, or torrenting. | More specific and can only handle HTTP/HTTPS requests. They are suitable for applications that require web browsing, web scraping, or accessing geo-restricted content. |
| Integration | More compatible and can work with any software that supports proxy settings. However, they may require additional configuration or authentication methods to set up. | More widely supported and can work with most web browsers and HTTP client libraries. However, they may not work with some software that uses other parameters, protocols, or ports. |
| Use in web scraping | Faster, more stable, and more secure than HTTP/HTTPS proxies. They can also bypass some firewalls and anti-scraping measures that block other proxy types. However, they are more expensive and less available. | Cheaper, more abundant, and easier to use. They can also cache web pages and reduce bandwidth consumption. However, they are more prone to blocking, throttling, and detection by anti-scraping measures. |
| Cost and accessibility | Generally more costly and less accessible than HTTP/HTTPS proxies. They have a limited pool of IP addresses and require higher maintenance. They are usually offered by premium proxy providers or specialized services. | Generally cheaper and more accessible than a SOCKS5 proxy. They have a larger pool of IP addresses and require less maintenance. They are widely offered by free proxy services or public proxy lists. |
| Setting up and configuration difficulty | More difficult to set up and configure. They may require manual configuration of the proxy protocol, port number, authentication method, and encryption mode. They may also need additional software or tools to work with some applications. | Easier to set up and configure than SOCKS proxies. They usually only require entering the proxy URL or IP address and port number in the proxy settings of the application. They may also have automatic detection or configuration options available. |
Why you should choose Infatica as your proxy provider
Infatica is a premium proxy provider that offers residential, datacenter, and mobile proxies for various purposes. Whether you need to scrape data, access geo-restricted content, verify ads, or automate social media, Infatica has the right proxy solution for you. Here are some of the key features that make Infatica proxies stand out from the rest:
99.9% uptime and low response time: Infatica’s proxy network is optimized for speed and performance. With high-bandwidth channels and robust server infrastructure, Infatica’s proxies maintain high uptime and low response time. This means you can access more URLs and send requests faster than your competitors.
Top speed and performance: Infatica’s proxies are fast, reliable, and scalable. They can use the HTTP protocol, as well as its variations and alternatives: HTTPS, FTP, SMTP, and UDP. They can also bypass firewalls, captchas, and anti-scraping measures that block other proxies. You can easily adjust the proxy settings to suit your needs and preferences.
Privacy and online security: Infatica’s proxies provide unhindered access to each of the portals without a captcha. The highest degree of user security, and reliable protection of important data from cyber-attacks, theft, or deletion. The system is tested for security automatically, which ensures continuous access to each information resource. When using Infatica’s proxies, your data is safeguarded with end-to-end encryption. Last but not least, you can choose between several authentication methods: the login/password or the address:port combo.
How to set up proxy manually
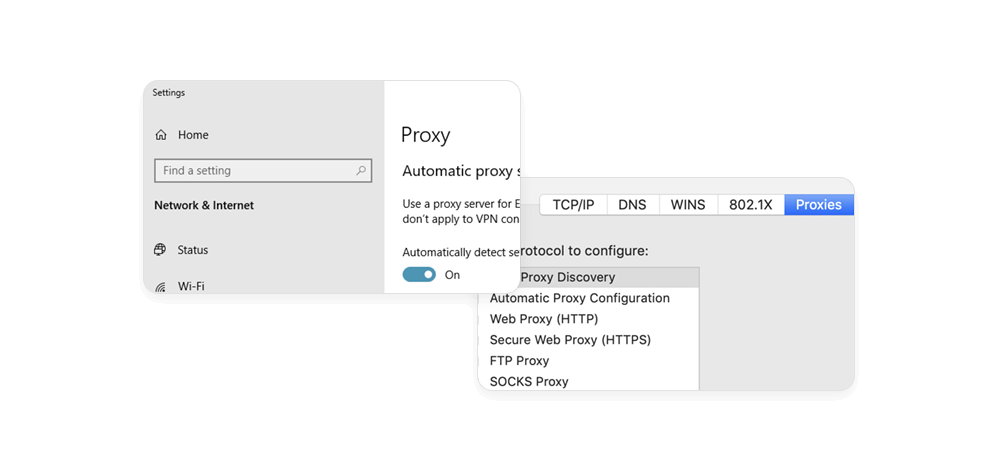
Adding a proxy configuration on the desktop is easy: You can install a proxy certificate, use a proxy management tool (e.g. FoxyProxy), or open your operating system’s settings menu – let’s take a closer look at the last option.
When setting up proxies manually, you’ll be asked to input the address and port. A proxy address is simply an IP address (e.g. 192.158. 1.38), while a proxy port number typically has four or five digits (e.g. 1080, 37192.)
Add a SOCKS5 proxy on Windows 10
- Open Windows Settings, select Network & Internet, and choose Proxy from the list on the left.
- Turn the “Manual proxy setup” option on.
- Input your proxy configuration into these fields: Address, Port.
- Click Save.
Add a SOCKS5 proxy on macOS
- Click the Apple logo to open System Preferences, select Network, choose Advanced → Proxies.
- From the list on the left, select SOCKS proxy.
- Add your proxy configuration (address, port) to the Web Proxy Server field.
- Click OK.
Add an HTTP/HTTPS proxy on Windows 10
- Open Windows Settings, select Network & Internet, and choose Proxy from the list on the left.
- Turn the “Manual proxy setup” option on.
- Input your proxy configuration into these fields: Address, Port.
- Click Save.
Add an HTTP/HTTPS proxy on macOS
- Click the Apple logo to open System Preferences, select Network, choose Advanced → Proxies.
- From the list on the left, select Web Proxy (HTTP) or Secure Web Proxy (HTTPS).
- Add your proxy configuration (address, port) to the Web Proxy Server field.
- Click OK.
Conclusion
In this article, we've analyzed two popular proxy types in great detail: We've outlined their pros, cons, and use cases; We've summarized their key differences in a easy-to-follow comparison table; We've learned how to add proxies to your Windows/macOS device manually. Happy scraping!








