
Proxies play a central role in these operations – and among the various types available, cloud proxies are becoming increasingly popular for their flexibility and ease of use. At Infatica, we’ve seen firsthand how organizations are turning to cloud-based proxies to meet evolving technical demands – from global data gathering to secure, location-specific browsing. Let’s explore how cloud proxies work, their advantages, and how they compare with traditional alternatives.
How Cloud Proxies Work
At their core, cloud proxies function like traditional proxies: they act as intermediaries between a user's device and the internet. However, what sets them apart is their deployment in cloud infrastructure, which brings added flexibility, scalability, and ease of management.
When a user sends a request (e.g., accessing a website or scraping a dataset), that request is routed through a proxy server hosted in the cloud. This server then forwards the request to the target destination, retrieves the response, and sends it back to the user – all while masking the user’s IP address and location. Because the proxy is cloud-hosted, it can be spun up, configured, or scaled in real time without the need for on-site hardware or manual setup.
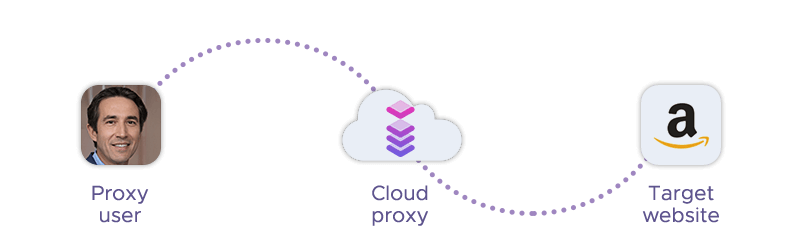
Cloud proxies typically rely on virtual machines or containerized environments, making it easy to deploy multiple proxy instances across different geolocations. This is especially useful for tasks that require global IP distribution, such as ad verification or localized search monitoring. Unlike locally deployed proxies, cloud proxies:
- Are centrally managed through user-friendly dashboards or APIs,
- Offer high availability thanks to redundant cloud systems,
- And support dynamic scaling, which is vital for high-volume operations.
At Infatica, we offer access to a robust cloud proxy infrastructure that simplifies this entire process – giving our users reliable, geo-distributed IPs without the operational complexity of managing proxy servers themselves.
Benefits of Using Cloud Proxies
Cloud proxies bring several key advantages that make them an attractive solution for businesses and developers alike – especially when managing large-scale, location-sensitive, or data-intensive operations:
Effortless Scalability
Because they’re built on cloud infrastructure, cloud proxies can be scaled up or down instantly to match your needs. Whether you're handling a burst of web scraping jobs or expanding into new markets, you won’t need to worry about hardware limitations or long deployment times.
Improved Security

Cloud proxies can also add a layer of security by acting as a buffer between the user and target websites. When configured properly, they can help prevent IP bans, mask traffic origin, and reduce exposure to malicious content.
High Availability and Reliability
Cloud providers typically operate multiple redundant systems across various regions, ensuring minimal downtime and fast failover in case of outages. As a result, cloud proxies deliver consistent uptime – a critical requirement for automated tasks and enterprise-grade workflows.
Geo-Flexibility
With cloud proxies, users can route traffic through servers in different countries or cities, allowing them to access geo-restricted content or simulate browsing from specific locations. This is especially valuable for market research, SEO monitoring, and content localization testing.
Simplified Management
Unlike traditional proxy setups that require manual configuration and upkeep, cloud proxies are often controlled via centralized dashboards or APIs. This allows teams to manage hundreds or thousands of proxies with minimal effort – and without touching any physical infrastructure.
Use Cases for Cloud Proxies
Cloud proxies enable critical functionality across a wide range of industries and use cases. Their flexibility, speed, and scalability make them especially valuable:
Web Scraping and Data Collection
Businesses use cloud proxies to gather public data at scale – from product pricing and customer reviews to market trends and real estate listings. By rotating IPs and using geo-targeted endpoints, scraping tools can avoid detection and access localized content without interruptions.
Ad Verification
To ensure ads are displayed correctly and free from fraud, advertisers use cloud proxies to simulate user behavior from various locations and devices. This lets them verify ad placement, detect spoofed impressions, and monitor unauthorized activity in real time.
SEO and SERP Monitoring
Companies track search engine rankings and keyword performance across different regions by routing queries through proxies in specific countries or cities. This allows for accurate SERP snapshots unaffected by personalization or location bias.
Bypassing Geo-Restrictions
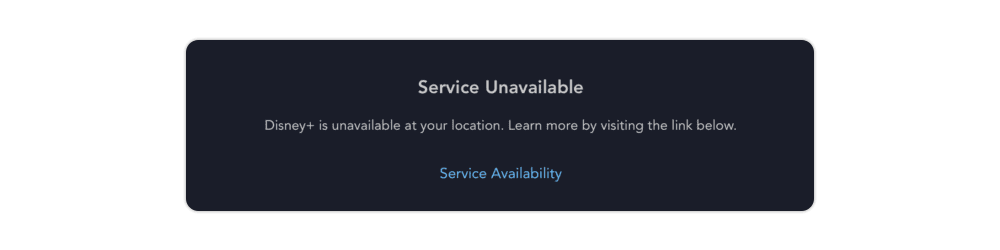
Cloud proxies enable users to access content that may be region-locked – whether for competitive research, QA testing, or content moderation. This is particularly useful for global platforms that need to understand how their services appear in different markets.
Brand Protection and Anti-Fraud
Cloud proxies help detect counterfeit listings, trademark misuse, or unauthorized resellers by allowing businesses to monitor third-party platforms without revealing their identity.
Cloud Proxies vs. Other Proxy Types
While “cloud proxy” refers to the deployment model, terms like “residential” or “datacenter” describe the origin of the IP address. In fact, residential and datacenter proxies can both be delivered via the cloud. Understanding these distinctions helps in selecting the right tool for your use case. The table below breaks down the key differences:
| Feature / Type | Cloud Proxy | Datacenter Proxy | Residential Proxy | Mobile Proxy |
|---|---|---|---|---|
| Definition | A proxy hosted in the cloud (not tied to IP type); can use residential or datacenter IPs | Proxy using IPs from data centers; often shared or static | Proxy using IPs from real residential devices | Proxy using IPs from mobile carriers (3G/4G/5G) |
| Deployment | Virtualized/cloud-hosted; scalable on demand | Hosted on physical servers | Routed through real household devices | Routed through real mobile devices |
| IP Origin | Datacenter or residential | Datacenter only | ISP-assigned residential connections | Carrier-assigned IPs |
| Scalability | Highly scalable | Moderate | Depends on peer availability | Limited; often low-scale |
| Anonymity / Stealth | Medium to high (depends on IP type used) | Low – easily detected as non-residential | High – hard to detect and block | Very high – trusted by most platforms |
| Speed | High | Very high | Moderate to high (varies) | Moderate |
| Use Cases | Web scraping, load testing, geo-access | Bulk scraping, SEO, market research | Ad verification, sneaker bots, local content | Mobile app testing, ad fraud detection |
Choosing the Right Cloud Proxy Provider
Not all cloud proxy providers are created equal. Whether you’re scraping data, verifying ads, or monitoring localized content, the right provider can mean the difference between smooth, scalable operations and constant disruptions. Let’s analyze the key factors to consider when selecting a cloud proxy provider:

IP Type and Pool Diversity
Ensure the provider offers the type of IPs you need – residential, datacenter, or mobile – with a wide geographic distribution. A diverse IP pool reduces the risk of bans and unlocks region-specific content.
✅ Infatica offers access to millions of residential and datacenter IPs across 190+ countries.
Performance and Reliability
Look for a provider with a proven track record of uptime, low latency, and stable connections. This is especially important for high-frequency or long-running tasks.
✅ Our cloud proxy infrastructure is built for reliability – with redundant systems and auto-scaling capacity to keep your requests running smoothly.
Proxy Management Tools
A good provider should offer intuitive management tools such as a self-service dashboard, usage analytics, IP rotation settings, and API integration.
✅ Infatica’s user dashboard and API let you control and monitor your proxy usage in real time.
Ethical and Legal Standards
Make sure the provider sources IPs ethically and complies with data privacy regulations. Using unethically sourced proxies can put your operation – and reputation – at risk.
✅ Infatica adheres to strict compliance practices and transparent IP sourcing.
Customer Support
Issues can arise unexpectedly, especially during large-scale operations. Responsive support ensures your team can get help quickly when it counts.
✅ Our support team is available 24/7 to assist with everything from setup to troubleshooting.